# fetch the kernel source code and extract it wget https://www.kernel.org/pub/linux/kernel/v3.x/linux-3.12.5.tar.xz tar Jxvf linux-3.12.5.tar.xz cd linux-3.12.5/ # prepare for the compilation, this will delete all current configuration and all generated files make mrproper # copy the config from the running system zcat /proc/config > .config # configure your customized kernel make menuconfig # Go to play some games # n for num of your process, e.g. make -j 8 make -j n # install modules under /lib/modules/ sudo make modules_install # prepare the new kernel under /boot/ sudo cp arch/x86_64/boot/bzImage /boot/vmlinuz-KernelName sudo mkinitcpio -k /boot/vmlinuz-KernelName -c /etc/mkinitcpio.conf -g /boot/initramfs-KernelName.img sudo cp System.map /boot/System.map-KernelName # update grub configuration sudo grub-mkconfig -o /boot/grub/grub.cfg
Thursday, December 19, 2013
Build Linux kernel from source
A note for building Linux kernel from source under Archlinux
Wednesday, September 4, 2013
Sunday, July 28, 2013
私人雲端動畫
最近研究了簡單的雲端動畫方案 (家裡網路... Orz)
當看完動畫時記得 sudo rm media 把 link 砍掉XD
transmission-remote + html5 (?)
實驗機器在 Ubuntu server上,有已經架好的 web server (apache)
Archlinux 的話裝這個套件 transmission-cli ,參考 Archwiki (不過東西有點少...)
sudo apt-get install transmission-daemon
sudo vim /etc/transmission-daemon/settings.json
一般來說會動到的參數大概有
# 如果你想把未完成分開的話可以開 true 並設好路徑
"incomplete-dir": "/home/xatier/Downloads",
"incomplete-dir-enabled": false,
"download-dir": "/home/xatier/Downloads",
# 加密一定要開的啦!LPD 是 Local Peer Discovery ,學校宿舍你懂得 (?)
"encryption": 1,
"lpd-enabled": true,
# 最重要的 rpc 設定
"rpc-password": "見底下說明",
"rpc-port": 9091,
"rpc-url": "/tran5mi55ion/",
"rpc-username": "bt",
"rpc-whitelist": "127.0.0.1,140.*.*.*",
"rpc-whitelist-enabled": true,
關於密碼的部份
rpc-password: The ssha1 encrypted password (starts with a '{') needed for remote access. A new password can be entered via command line utilities or directly in plain text and will replaced with the encrypted version when the configuration file is next saved.
白名單用逗號隔開,可用 * 當 wildcard
transmission 有自己的 web-UI ,rpc 白名單設好後直接連你設的 port 就 ok 惹
官網有截圖就不再贅述
另外也可以裝 transmission-remote-gui 可以直接調整更多設定
接著,原本想弄個 web 網站可以選要看的動畫之類的
HTML5 有個 <video> tag 可以直接放,許多瀏覽器有支持
後來覺得只是脫褲子放屁,因為有更簡單的方法XD
# web server 的 root directory
cd /var/www
sudo ln -s /home/xatier/Downloads/ media
http://mydomain.com/media/[KT*P][Shing*ki no Kyojin][15][BIG5][720p][MP4].mp4
就可以看啦XDDD
當看完動畫時記得 sudo rm media 把 link 砍掉XD
這麼簡單的作法可以拿個 raspberry pi 當農場機加上 streaming 源之類的XD
Saturday, July 20, 2013
HIT2013 解題心得
今年因為一些緣故,所以無法到會場參加每年安全最大的盛會 hitcon
雖然一開始搶票的時候沒弄到,連幹了活X通幾聲
然而,幸運的在今年 PyCON 2013 中午看到 @crboy 小畢發噗,說也來寫個哀怨的對聯好了XDD
創意對聯
Cyberwar: in hack, we trust
Ticketwar: at midnight, the site crashed
橫批:Distributed Denial of Service
沒想到... 就拿到票惹XD
Anyway, 來寫心得文吧!XD
今年題目設計和以往又有些不同,多了很多 AppleScript/Obj-C 的 hacking, PE / .NET 逆向題目也不錯,.apk 也許也該來碰了...XD
各題首次破台者
媽我在這~~~._./
最終盤面
稍作整理然後轉成 binary
echo -n -e $(tr -d '[:space:]' | sed 's/../\\x&/g')
$ file new.bin
new.bin: PE32 executable for MS Windows (console) Intel 80386 32-bit

這個東西拿到 VM 底下就一隻該死的南瓜... Orz (而且還會唱歌www)
而且還需要用 upx 去個殼...
strings 結果:
字串都不是 key
IDA 看了很久也沒有想法,丟給隊友作,後來據說是解神奇的數學 (?
這題乍看之下要分析 JavaScript (小弟苦手...
而且還是 aaencode ゚ω゚ノ= /`m´)ノ ~┻━┻
不過... 其實秘訣就... 讓那段 code 動起來XDD
strings 結果:
字串都不是 key
IDA 看了很久也沒有想法,丟給隊友作,後來據說是解神奇的數學 (?
解!
這題乍看之下要分析 JavaScript (小弟苦手...
而且還是 aaencode ゚ω゚ノ= /`m´)ノ ~┻━┻
不過... 其實秘訣就... 讓那段 code 動起來XDD
chrome console 下,var foo = function {......}
foo();
就拿到 key 啦!還會有動畫XDDDD
Web 苦手,pass 給隊友 Orz
社交工程 pf ㄉㄉ也可以拿到 key
foo();
就拿到 key 啦!還會有動畫XDDDD
解!
Web 苦手,pass 給隊友 Orz
這題其實www
乍看之下 py2exe 要反解... 不過就...
unzip + vim 搞定XD
strings 出來的解和這邊一樣...
http://stuff.mit.edu/afs/sipb/project/hurddev/tb/libc/locale/C-identification.c
http://svn.haiku-os.org/oldhaiku/haiku/branches/old/wcsmbs/current/src/kernel/libroot/posix/glibc/wcsmbs/wcsmbsload.c
這個也殘念,exploit pdf 先丟反解把 pdf decode 成明碼
用和這邊 類似的作法,可是沒找到可疑的 JavaScript ...
Pass
隊友 TW1943 完成
rar fixnul.Ly
crack md5
Philippines
得意解!!!!!
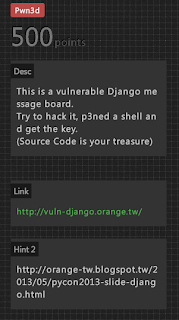
PyCON.tw 2013 時,Orange 在 "駭客看 Django" 的議程上特別說過,Secret key 很重要,可以用來偽造 Cookie 達成許多不可思議的事情
Google 找攻略,這邊有詳細介紹這類的攻擊方式
首先 clone 這個 repo 下來
connback.py 改成自己的機器,做反彈 shell
然後
./exploit.py "1%idg#a2%byqh@l1wcv^3kc=e*($0v44(u-c^@bf_lz-@#essk" http://vuln-django.orange.tw
到處看看
./exploit.py "1%idg#a2%byqh@l1wcv^3kc=e*($0v44(u-c^@bf_lz-@#essk" http://vuln-django.orange.tw
到處看看
# cat ./app/key.txt
看到後底下回個 QQ ...
沒想到 12 分鐘後就 done 了XDDDD
解完這題很開心,一度名次還沒前面的說QQ
我解完 PWN500 後自己測試帳號是第四名XDD
Tuesday, July 16, 2013
touch? no! just use the redirection!
大家都知道,要創建一個新檔案就是讓哥哥摸一下
$ touch foo
不過其實有更快的方法
$ > foo
$ :> foo # happy face!
> 是大家都知道的 redirection,把空 redirect 到(不存在的)文件也就是創造新檔案
: 是 bash 裡面的空函數(?)
$ man bash
: [arguments]
No effect; the command does nothing beyond expanding arguments and performing any specified redirections. A zero exit code is returned.
$ touch foo
不過其實有更快的方法
$ > foo
$ :> foo # happy face!
> 是大家都知道的 redirection,把空 redirect 到(不存在的)文件也就是創造新檔案
: 是 bash 裡面的空函數(?)
$ man bash
: [arguments]
No effect; the command does nothing beyond expanding arguments and performing any specified redirections. A zero exit code is returned.
Monday, July 15, 2013
bash: tab-completion case insensitive
習慣一直戳 [Tab] 是大家的好習慣 (?)
但是要按 shift 實在是很麻煩,於是乎
$ sudo vim /etc/inputrc
set completion-ignore-case on
$ man bash
completion-ignore-case (off)
If set to On, readline performs filename matching and completion in a case-insensitive fashion.
但是要按 shift 實在是很麻煩,於是乎
$ sudo vim /etc/inputrc
set completion-ignore-case on
$ man bash
completion-ignore-case (off)
If set to On, readline performs filename matching and completion in a case-insensitive fashion.
Wednesday, July 3, 2013
Archlinux Android USB Tethering
USB Tethering: 透過 USB 把網路從 Android 設備弄到 Linux 上
Ref: https://wiki.archlinux.org/index.php/Android_Tethering
Steps:
1. load the usbnet kernel module
2. set up the interface
3. run dhcpcd
sudo modprobe usbnet
ifconfig -a # find something like usb0
sudo ip link set usb0 up
sudo dhcpcd usb0
Ref: https://wiki.archlinux.org/index.php/Android_Tethering
Steps:
1. load the usbnet kernel module
2. set up the interface
3. run dhcpcd
sudo modprobe usbnet
ifconfig -a # find something like usb0
sudo ip link set usb0 up
sudo dhcpcd usb0
Monday, July 1, 2013
keyboard setting om OS X
我有個 filco 青軸,接在 Air 上面需要作一些 keyboard layout 的調整
我的 control 和 capslock 是交換的,並且 Alt/Command 在 Mac 鍵盤上是和一般鍵盤的順序是相反的。
如以下方式調整
我的 control 和 capslock 是交換的,並且 Alt/Command 在 Mac 鍵盤上是和一般鍵盤的順序是相反的。
如以下方式調整
Thursday, June 27, 2013
git archive to tarballs
今天看到的小工具,git 可以直接把整個 repo 打包帶走
git archive --format=tar --prefix=proj-1.2.3/ HEAD > proj-1.2.3.tar
Ref/
https://www.kernel.org/pub/software/scm/git/docs/git-archive.html
Wednesday, June 26, 2013
let wget ignore robots.txt
我們可以寫 robots.txt 來防止機器人或是 crawler 亂爬我們的網站
wget 是很遵守 robots.txt 的,不過還是有方法可以偽裝我們不是機器人
wget -e robots=off [url]
-e 是可以附加在 wgetrc 中沒寫的功能
--execute command
Execute command as if it were a part of .wgetrc. A command thus invoked will be executed after the commands in .wgetrc, thus taking precedence over them. If you need to specify more than one wgetrc command, use multiple instances of -e.
Reference
http://www.gnu.org/software/wget/manual/html_node/Robot-Exclusion.html
wget 是很遵守 robots.txt 的,不過還是有方法可以偽裝我們不是機器人
wget -e robots=off [url]
-e 是可以附加在 wgetrc 中沒寫的功能
--execute command
Execute command as if it were a part of .wgetrc. A command thus invoked will be executed after the commands in .wgetrc, thus taking precedence over them. If you need to specify more than one wgetrc command, use multiple instances of -e.
Reference
http://www.gnu.org/software/wget/manual/html_node/Robot-Exclusion.html
Thursday, June 6, 2013
Tuesday, May 14, 2013
Perl undefined array / hash
要把 array 和 hash 清掉一樣有兩種作法
@array = ();
%hash = ();
undef @array;
undef %hash;
簡單的名詞解釋:
An array is initialized or not ->
簡單的名詞解釋:
An array is initialized or not ->
call scalar() to check the number of elements or call defined()
if scalar() return false (the number of elements) is 0, then the array is uninitialized.
但是以下是錯誤示範
This would fill the array with one element at index zero with a value of undefined.
equal to $array[0] = undef;
my @array = undef; # WRONG!!!!
Round floating points in Perl
四捨五入是很常見的問題
Perl 中有兩種簡單的方法可以達到:
一種是加上 0.5 後取 int() (positive numbers)
另一種是 sprintf 用 %.0f 控制
不過浮點數本身便有其限制,預設的浮點數在高精度需求的運算是無意義的
底下的範例可以看到,當要求很高的精度時,會有誤差需小心
Perl 中有兩種簡單的方法可以達到:
一種是加上 0.5 後取 int() (positive numbers)
另一種是 sprintf 用 %.0f 控制
不過浮點數本身便有其限制,預設的浮點數在高精度需求的運算是無意義的
底下的範例可以看到,當要求很高的精度時,會有誤差需小心
use 5.016; say int(9.9+0.5); # 10 say int(9.50000000+0.5); # 10 say int(9.49999999+0.5); # 9 say int(9.49999999999999+0.5); # 9 say int(9.49999999999999999999+0.5); # 9? say "-"x20; say sprintf("%0.f", 9.9); # 10 say sprintf("%0.f", 9.50000000); # 10 say sprintf("%0.f", 9.49999999); # 9 say sprintf("%0.f", 9.499999999999999); # 9 say sprintf("%0.f", 9.49999999999999999999); # 9? =output 10 10 9 9 10 -------------------- 10 10 9 9 10 =cut
Wednesday, May 1, 2013
Python format string
更多請參考: PEP-3101
基本的 format string 使用方法:
排版:
The general form of a standard format specifier is:
[[fill]align][sign][#][0][minimumwidth][.precision][type]
The brackets ([]) indicate an optional element.
基本的 format string 使用方法:
# basic In [1]: "Hello, {}".format("xatier") Out[1]: 'Hello, xatier' # {0} means the first argument in format() In [2]: "Hello, {0}".format("xatier") Out[2]: 'Hello, xatier' # {1} means the second argument In [3]: "{1} {0}".format("xatier", 3) Out[3]: '3 xatier' # pass arguments one by one In [4]: "{} {}".format("xatier", 3) Out[4]: 'xatier 3' # use doubled { to represent '{' In [5]: "{} {{".format("xatier") Out[5]: 'xatier {' # get item: use [] to get fields in a dictionary In [10]: my_dog = {'name': "Jack", 'age': 3} In [11]: "My dog's name: {0[name]}, {0[age]} years old.".format(my_dog) Out[11]: "My dog's name: Jack, 3 years old." # do the same thing in an anonymous dictionary In [15]: "My name is {0[name]}".format({'name': 'Fred'}) Out[15]: 'My name is Fred' In [16]: "My name is {0[name]}".format(dict(name='Fred')) Out[16]: 'My name is Fred' # get attribute: use '.' to get attributes in a class/object In [18]: import sys In [19]: "{0.stdin}".format(sys) Out[19]: "<open file '<stdin>', mode 'r' at 0x7f88ecd94150>" In [20]: "{0.stdin.write}".format(sys) Out[20]: '<built-in method write of file object at 0x7f88ecd94150>' # get object's data In [30]: class Foo: ....: def __init__(self, name="yoo"): ....: self.name = name ....: In [31]: a = Foo() In [32]: "{0.name}".format(a) Out[32]: 'yoo' In [33]: a = Foo("my name ^.<") In [34]: "{0.name}".format(a) Out[34]: 'my name ^.<' Only two operators are supported: the '.' (getattr) operator, and the '[]' (getitem) operator. The reason for allowing these operators is that they don't normally have side effects in non-pathological code.
排版:
The general form of a standard format specifier is:
[[fill]align][sign][#][0][minimumwidth][.precision][type]
The brackets ([]) indicate an optional element.
# fill with space In [42]: "My name is {0:8}".format('Fred') Out[42]: 'My name is Fred ' # string force to left/right In [44]: "My name is {0:<8}".format('Fred') Out[44]: 'My name is Fred ' In [45]: "My name is {0:>8}".format('Fred') Out[45]: 'My name is Fred' # floating point In [72]: "{0:f}".format(123.45) Out[72]: '123.450000' In [73]: "{0:.3f}".format(123.45) Out[73]: '123.450' In [75]: "{0:>10.3f}".format(123.45) Out[75]: ' 123.450' # show the + sign In [76]: "{0:>+10.3f}".format(123.45) Out[76]: ' +123.450' In [77]: "{0:<+10.3f}".format(123.45) Out[77]: '+123.450 ' # = means fill with In [78]: "{0:<=10.3f}".format(123.45) Out[78]: '<<<123.450' In [79]: "{0:A=10.3f}".format(123.45) Out[79]: 'AAA123.450' In [80]: "{0:0=10.3f}".format(123.45) Out[80]: '000123.450'
Tuesday, April 30, 2013
Python string permutation
很多時候需要有枚舉一串字的需求
Python 內建的 itertools 其實就有內建了
再加上 generator 語法可以很簡單的解決問題
"".join 是常用的 list->string 的標準作法,因為原本拿出來的結果是一個個的 tuple
Python 內建的 itertools 其實就有內建了
再加上 generator 語法可以很簡單的解決問題
In [1]: import itertools In [2]: S = "abc" In [3]: ("".join(i) for i in (itertools.permutations(sorted(S)))) Out[3]: <generator object <genexpr> at 0x1aa02d0> In [4]: print ["".join(i) for i in (itertools.permutations(sorted(S)))] ['abc', 'acb', 'bac', 'bca', 'cab', 'cba'] In [5]: for i in ("".join(i) for i in (itertools.permutations(sorted(S)))): print i, abc acb bac bca cab cba
"".join 是常用的 list->string 的標準作法,因為原本拿出來的結果是一個個的 tuple
In [6]: list(i for i in (itertools.permutations(sorted(S)))) Out[6]: [('a', 'b', 'c'), ('a', 'c', 'b'), ('b', 'a', 'c'), ('b', 'c', 'a'), ('c', 'a', 'b'), ('c', 'b', 'a')]
Sunday, April 28, 2013
Perl Dumpvalue
Perl 寫程式時,常遇到複雜物件的處理,尤其是從 CPAN 上面拿到的 modules 有的 doc 往往標示不清,要用時不確定物件的確實結構,不知如何下手。
除了 Data::Dumper 以外,今天看到 Dumpvalue 這個也是內建的好用物件解析工具
使用方法:
output:
Ref.
perldoc lol
http://perldoc.perl.org/Dumpvalue.html
除了 Data::Dumper 以外,今天看到 Dumpvalue 這個也是內建的好用物件解析工具
使用方法:
#!/usr/bin/perl use 5.014; sub show { require Dumpvalue; state $prettily = Dumpvalue->new( compactDump => 1, veryCompact => 1); state $ugly = Dumpvalue->new(); say "-"x40; $prettily->dumpValue(\@_); say "-"x30; $ugly->dumpValue(\@_); say "-"x40; } my @AoA = [[1, 2, 3], [4, 5, 6], [7, 8, 9]]; my @AoH = ({1 => 2}, {2 => 3}, {3 => 4}); show(@AoA); show(@AoH);
output:
----------------------------------------
0 ARRAY(0x9661910)
0 0..2 1 2 3
1 0..2 4 5 6
2 0..2 7 8 9
------------------------------
0 ARRAY(0x9661910)
0 ARRAY(0x9653068)
0 1
1 2
2 3
1 ARRAY(0x9653c58)
0 4
1 5
2 6
2 ARRAY(0x9653d18)
0 7
1 8
2 9
----------------------------------------
----------------------------------------
0 1 => 2
1 2 => 3
2 3 => 4
------------------------------
0 HASH(0x9653c68)
1 => 2
1 HASH(0x9661ad0)
2 => 3
2 HASH(0x9661b10)
3 => 4
----------------------------------------
Ref.
perldoc lol
http://perldoc.perl.org/Dumpvalue.html
Python bytearray
在寫接近 C 的想法時,會想要在 Python 使用想是 C 的 array of char
之前一直為這個問題困擾很久,因為我只會用 Python string XD
看了點攻略,其實有這個可以用
於是乎就可以爽爽的用可變長度的 array of char in python 啦~
In [18]: a = bytearray(b'\x41\x42\x43\x44') # create 'ABCD' in array of bytes In [19]: a Out[19]: bytearray(b'ABCD') In [20]: a.lower() # to lowercase Out[20]: bytearray(b'abcd') In [21]: a[0] = 0x45 # assign values just like char[] in C language In [22]: a Out[22]: bytearray(b'EBCD') In [23]: a.decode('ascii') # get a string in ASCII Out[23]: 'EBCD' In [24]: a.append(ord('F')) # variable length In [25]: a Out[25]: bytearray(b'EBCDF')
很棒的是,基本上 string 的方法都可以用
In [27]: bytearray.
bytearray.append bytearray.isalnum bytearray.mro bytearray.split
bytearray.capitalize bytearray.isalpha bytearray.partition bytearray.splitlines
bytearray.center bytearray.isdigit bytearray.pop bytearray.startswith
bytearray.count bytearray.islower bytearray.remove bytearray.strip
bytearray.decode bytearray.isspace bytearray.replace bytearray.swapcase
bytearray.endswith bytearray.istitle bytearray.reverse bytearray.title
bytearray.expandtabs bytearray.isupper bytearray.rfind bytearray.translate
bytearray.extend bytearray.join bytearray.rindex bytearray.upper
bytearray.find bytearray.ljust bytearray.rjust bytearray.zfill
bytearray.fromhex bytearray.lower bytearray.rpartition
bytearray.index bytearray.lstrip bytearray.rsplit
bytearray.insert bytearray.maketrans bytearray.rstrip
Ref. https://www.inkling.com/read/learning-python-mark-lutz-4th/chapter-36/using-3-0-and-2-6-bytearray
Friday, April 26, 2013
qsort in Python/Perl
社窩開始了 python 練習
題目是 qsort
其實就是最簡單的想法,分兩堆然後相加
第一次寫的方法是用 filter, 不過某 apua 說要用 list comprehension 才潮,所以 XD
然後後來寫了 Perl 版
Python
Perl
其實這想法很 FP,以下可以看看 Haskell code XD
Haskell
題目是 qsort
其實就是最簡單的想法,分兩堆然後相加
第一次寫的方法是用 filter, 不過某 apua 說要用 list comprehension 才潮,所以 XD
然後後來寫了 Perl 版
Python
q = lambda l: (q(filter(lambda x: x > l[0], l)) + [l[0]] + q(filter(lambda x: x < l[0], l)) if l else []) q = lambda l: ((q([ x for x in l if x > l[0]]) + [l[0]] + q([ x for x in l if x < l[0]])) if l else []) print q([3, 5, 1, 2, 4, 7, 89, 9, 10])
Perl
sub qs { @_ ? (qs(grep {$_ > $_[0]} @_), $_[0], qs(grep {$_ < $_[0]} @_)): (); } say join(", ", qs(10, 6, 2, 6, 2, 6, 4, 1, 3));
其實這想法很 FP,以下可以看看 Haskell code XD
Haskell
qsortOneLine s = case s of{[]->[];(x:xs)->qsortOneLine [y | y<-xs, y<x] ++ x : qsortOneLine [y | y<-xs, y>=x]}
Thursday, April 18, 2013
ip tools note
ifconfig 和一些 tools 已經要漸漸被拿掉了
整理一些用法
ref.
wiki.archlinux.org Network Configuration
wiki.archlinux.org VLAN
整理一些用法
old -> new
=====================================
arp -> ip n (ip neighbor)
ifconfig -> ip l (ip link)
ip a (link addr)
iptunne -> ip tunnel
iwconfig -> iw
netstat -> ss
ip route (for netstat-r)
ip -s link (for netstat -i)
ip maddr (for netstat-g) (multicast address)
route -> ip r (ip route)
ip link # <if>: interface something like 'enp2s0'
ip link set <if> up # switch <if>
ip link set <if> down
ip link show dev <if> # show <if>
ip link set dev <if> mtu 1400 # set mtu
ip link add link eth0 name eth0.10 type vlan id 10 # create vlan
ip link delete dev eth0.10 # delete vlan
ip addr add <ip address>/<subnetmask> dev <if> # add address
ip addr del <ip address>/<subnetmask> dev <if> # delete address
ip addr show dev <if> # show address
ip addr flush dev <if> # removes all addresses from device <if>
ip route add default via <gateway's ip address> # add a routing path
ip route add - add new route
ip route change - change route
ip route replace - change or add new one
ref.
wiki.archlinux.org Network Configuration
wiki.archlinux.org VLAN
miyagawa says good luck to me
非常崇拜的日本 hacker miyagawa 親自為我期中考加油耶!!!!
潮爽的~~~
潮爽的~~~
14:30 | darkx > 可惜明天無法到場,否則真的很想聽 miyagawa 的 talk 14:31 | miyagawa > darkx: hmm too bad! 14:31 | darkx > :) 14:33 | FourDollars > miyagawa: You can read Chinese! Awesome! 14:33 | miyagawa > 繁体字 is easier to read :) 14:33 | miyagawa > still often needs google translate though 14:33 | FourDollars > haha 14:34 | darkx > I have to take my midterm exam tomorrow, but still really excited about your talk! 14:34 | miyagawa > darkx: good luck! 14:35 | darkx > miyagawa: cpanm is an excellent tool for we Perl users, it rocks!
Monday, April 8, 2013
bitcoin mining
bitcoin 應該是愈來愈重要的東西了... 所以及早入場(?
http://bitcoin.org/en/
最簡單的方法是到 pool 裏面跟大家一起挖
pools 有很多種,我是到這邊
https://mining.bitcoin.cz
然後裝 cgminer 就好了
$ git clone https://github.com/ckolivas/cgminer.git
$ cd cgminer
$ ./autogen.sh
# enable CPU mining
$ ./configure --enable-cpumining
$ make
$ sudo make install
$ cgminer -o http://api.bitcoin.cz:8332 -u <user> -p <password>
為了避免影響到其他工作可以 renice 它
$ ps aux | grep cgminer
http://bitcoin.org/en/
最簡單的方法是到 pool 裏面跟大家一起挖
pools 有很多種,我是到這邊
https://mining.bitcoin.cz
然後裝 cgminer 就好了
$ git clone https://github.com/ckolivas/cgminer.git
$ cd cgminer
$ ./autogen.sh
# enable CPU mining
$ ./configure --enable-cpumining
$ make
$ sudo make install
$ cgminer -o http://api.bitcoin.cz:8332 -u <user> -p <password>
為了避免影響到其他工作可以 renice 它
$ ps aux | grep cgminer
$ renice 19 <pid>
Thursday, March 21, 2013
Emacs: Flyspell-mode
最近開始拿 Emacs 編寫上課筆記,像我這種英文苦手表示悲劇,常常拼錯自,好在 Emacs 有內建的 flyspell-mode 可以幫我解決這個問題
http://www.emacswiki.org/emacs/FlySpell
在 .emacs 裡面加入 (或是用 hook 綁在某個 mode 上)這行即可
(flyspell-mode 1)
M-TAB 可以幫你 auto correct 回來,就甘心
Tuesday, March 5, 2013
Python dump skype DB
據說 Skype local 端資料也是直接用 sqlite 存的
Mac OSX
~/Library/Application Support/Skype/$account/main.db
Linux
~/.Skype/$account/main.db
所以我們可以自己寫 tools 查看自己的資料請不要拿來查看別人的資料 >_<
剛剛初步可以 Dump 出以下XD
也許這樣學習資料庫比較有趣(?
Sample code:
Mac OSX
~/Library/Application Support/Skype/$account/main.db
Linux
~/.Skype/$account/main.db
所以我們可以自己寫 tools 查看自己的資料
剛剛初步可以 Dump 出以下XD
也許這樣學習資料庫比較有趣(?
[~/.Skype/****]-[Arch Linux] $ sqlite3 main.db SQLite version 3.7.15.2 2013-01-09 11:53:05 sqlite> .table Accounts ChatMembers Conversations Participants Videos Alerts Chats DbMeta SMSes Voicemails CallMembers ContactGroups LegacyMessages Transfers Calls Contacts Messages VideoMessages sqlite> select * from Accounts;
Sample code:
#!/usr/bin/python import sys import sqlite3 def printProfile(skypeDB): conn = sqlite3.connect(skypeDB) c = conn.cursor() print "show tables:" c.execute("SELECT tbl_name from sqlite_master WHERE type=='table';") print c.fetchall() c.execute("SELECT fullname, skypename, city, country, \ datetime(profile_timestamp,'unixepoch') FROM Accounts;") print "Dump Account: " print "-" * 50 for row in c.fetchall(): print '[*] -- Found Account --' print ' [+] User: ' + row[0] print ' [+] Skype Username: ' + row[1] print ' [+] Location: ' + row[2] + ',' + row[3] print ' [+] Profile Date: ' + row[4] print "Dump Contacts: " print "-" * 50 c.execute("SELECT displayname, skypename, phone_mobile, \ birthday FROM Contacts;") for row in c.fetchall(): print '[*] -- Found Account --' print ' [+] User: ' + (row[0]) print ' [+] Skype Username: ' + row[1] print ' [+] Phone_mobile: ' + str(row[2]) print ' [+] Birthday: ' + str(row[3]) if __name__ == "__main__": printProfile(sys.argv[1])
python nmap
Ref: http://xael.org/norman/python/python-nmap/
https://pypi.python.org/pypi/python-nmap/0.2.7
知己知彼,百戰百勝,nmap 是什麼這邊就不多作介紹了
python-nmap 是一個 nmap 的 python wrapper ,用於方便對於 namp 操作
也許今天有好多好多機器需要作測試,pyhton-nmap 這時就是我們的好工具了
高階邏輯的部份,例如決定哪些機器需要作測試、測試的 policy 、結果分析等等
這些事情可以丟給 python 解決,而不用痛苦的在 shell scripts 裡面完成這些苦工
Sample code:
'''
methods:
nm.all_hosts nm.get_nmap_last_output
nm.nmap_version nm.scanstats nm.command_line
nm.has_host nm.scan
nm.csv nm.listscan
nm.scaninfo
nm.scan()
Definition: nm.scan(self, hosts='127.0.0.1', ports=None, arguments='-sV')
hosts = string for hosts as nmap use it 'scanme.nmap.org' or '198.116.0-255.1-127' or '216.163.128.20/20'
ports = string for ports as nmap use it '22,53,110,143-4564'
arguments = string of arguments for nmap '-sU -sX -sC'
maybe need root privileges
PortScannerError: u'You requested a scan type which requires root privileges.\nQUITTING!\n'
'''
個人認為,在 iPython 裡面用這玩意超好用的XD
同場加映 Perl 也有人作類似的 CPAN module
http://search.cpan.org/~maxschube/Nmap-Scanner-1.0/
https://pypi.python.org/pypi/python-nmap/0.2.7
知己知彼,百戰百勝,nmap 是什麼這邊就不多作介紹了
python-nmap 是一個 nmap 的 python wrapper ,用於方便對於 namp 操作
也許今天有好多好多機器需要作測試,pyhton-nmap 這時就是我們的好工具了
高階邏輯的部份,例如決定哪些機器需要作測試、測試的 policy 、結果分析等等
這些事情可以丟給 python 解決,而不用痛苦的在 shell scripts 裡面完成這些苦工
Sample code:
#!/usr/bin/python import nmap nm = nmap.PortScanner() result = [] result.append( nm.scan('127.0.0.1', ports='22-443') ) result.append( nm.scan('127.0.0.1', arguments='-p22-443') ) result.append( nm.scan('localhost', arguments='-sT')) result.append( nm.scan(arguments='-p 0-1024') ) result.append( nm.scan(arguments='-p22 -sV') ) for r in result: print r print "=" * 50
'''
methods:
nm.all_hosts nm.get_nmap_last_output
nm.nmap_version nm.scanstats nm.command_line
nm.has_host nm.scan
nm.csv nm.listscan
nm.scaninfo
nm.scan()
Definition: nm.scan(self, hosts='127.0.0.1', ports=None, arguments='-sV')
hosts = string for hosts as nmap use it 'scanme.nmap.org' or '198.116.0-255.1-127' or '216.163.128.20/20'
ports = string for ports as nmap use it '22,53,110,143-4564'
arguments = string of arguments for nmap '-sU -sX -sC'
maybe need root privileges
PortScannerError: u'You requested a scan type which requires root privileges.\nQUITTING!\n'
'''
個人認為,在 iPython 裡面用這玩意超好用的XD
同場加映 Perl 也有人作類似的 CPAN module
http://search.cpan.org/~maxschube/Nmap-Scanner-1.0/
Python image downloader
昨天下午寫出來的小玩具
BeautifulSoup 和 urllib2 的簡單練習 : )
然後我發現我還是不會用 Python 的 re .... Orz
絕對不是要拿來抓謎物喔
BeautifulSoup 和 urllib2 的簡單練習 : )
然後我發現我還是不會用 Python 的 re .... Orz
#!/usr/bin/python import urllib2 import urlparse import BeautifulSoup import os import time import re def find_tags(url): c = urllib2.urlopen(url).read() soup = BeautifulSoup.BeautifulSoup(c); return soup.findAll('img') def get_src(url, re_): r = re.compile(re_) tags = find_tags(url) for tag in tags: img = tag['src'] if r.search(img): yield img def get_basename(url): return os.path.basename(urlparse.urlsplit(url)[2]) def download(url, re_=''): for src in get_src(url, re_): content = urllib2.urlopen(src).read() print "[+] download: " + src file_ = open(get_basename(src) , 'wb') file_.write(content) file_.close() time.sleep(1) if __name__ == '__main__': download(url='http://this-plt-life.tumblr.com', re_='gif')
Subscribe to:
Posts (Atom)